How to Become PCI Compliant: List for Apps and Websites
Updated 01 May 2023
16 Min
2950 Views
Service providers and retailers set their course for digitalization. According to Statista, the overall revenue of digital technologies will reach $2.3 billion by 2023. Such an impressive number shows that customers value the convenience of digital services and feel safe while paying for them online. However, there are a series of requirements to the systems that are responsible for the safety of users.
PCI DSS is the main standard that safeguards users’ payment card details. It obliges app owners to audit the secureness of their software and validate the compliance to PCI DSS. In this post, we’ll help you figure out how to get PCI DSS compliance, what are PCI DSS requirements, and explain how this standard works on different platforms.
Why Is PCI DSS Important and When Do You Need It?
Before we get to the topic, you should get a better understanding of what PCI DSS is and what its origin story is.
PCI DSS: fast history lesson
PCI DSS stands for Payment Card Industry Data Security Standard. Back in the 90s, there was no unified standard that’d ensure the security of sensitive data for a long time. Every payment system like Visa, MasterCard, American Express, Discover, and JCB had their own security protocols with minimal requirements. The Payment Card Industry Security Standard Council appeared some time later and launched the first version of PCI DSS 2004. The protocol had minimum requirements to all parties that hold, transmit, and process credit card data. With the rapid development of cloud technologies and increased demand in online payments, PCI DSS evolved into a full-fledged protocol that set high standards of handling sensitive data.
The latest version of PCI DSS is v4.0, released in March 2022. The previous standard, PCI DSS v3.2.1, will be in effect two years after the new version is released, allowing for a smoother transition. The PCI Security Standards Council recommends studying the new standard, reviewing and updating your templates and forms accordingly, and focusing on adopting the major changes to prepare for PCI DSS v4.0 compliance.
Being PCI compliant is critical because you can understand where to start creating your security program and what to do in case of a potential security breach. It also provides guidelines to help you know how to handle your customer data.
Software that requires PCI DSS
As for now, every payment system and software that works with credit card data should become PCI DSS compliant by default. Violations may lead to customer data leakage and large fines for your company. Fines range from $5,000 to $100,000 per month depending on the business size and the type of non-compliance.
However, the PCI DSS compliance process has some strict regulations that demand deep technical expertise in the first place. Adjusting the network, setting up firewalls, keeping track of access to the data, and more. To handle all these, you should hire experienced tech specialists.
Compliance levels
The requirements may vary depending on the number of clients you serve and the number of transactions you process annually. There are four PCI DSS compliance levels for trading and service enterprises that accept credit cards as payment methods.
Now, let’s single out each of them.
- Level 1 — over 6 million of Visa or Mastercard transactions per year or 2.5 million transactions of American Express per year. This PCI DSS level can also be applied to companies that experienced a security breach before. Each year a Qualified Security Assessor or a certified internal employee conducts an audit and writes an Annual Report on Compliance according to this template. Besides, an approved company conducts a quarterly network scan to detect vulnerabilities.
- Level 2 — between 1 and 6 million transactions per year. This level of compliance obliges companies to conduct an annual PCI DSS assessment and fill in the questionnaire. Annual ASV scanning is also required.
- Level 3 — between 20,000 and 1 million transactions per year. The overall requirements are similar to those for level 2.
- Level 4 — under 20,000 transactions. The overall requirements are similar to those for levels 2 and 3.
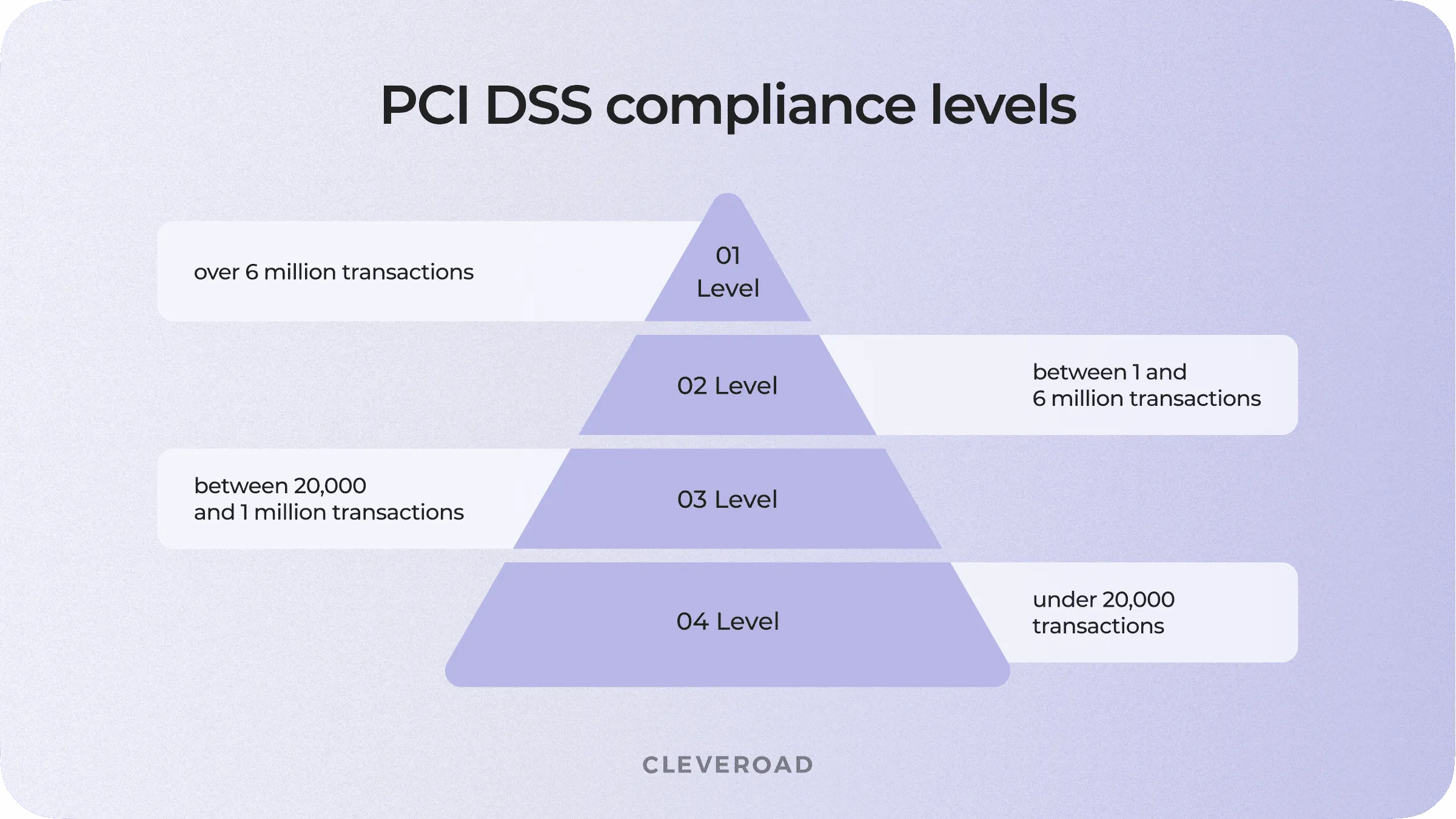
4 levels of PCI DSS compliance
Third-party payment gateways
If you’re looking for a less challenging way to integrate payments into your app, you can make use of payment gateways. Payment gateways like PayPal, Stripe, Braintree take care of all operations related to payment details and save a lot of time and money.
Let’s take a closer look at Stripe. It provides its own API that handles all transfer-related operations. Technically, app owners don’t have to worry about building their own payment system and keep user data safe. With Stripe, entrepreneurs don’t have to store card numbers, CVV codes, expiration dates, and cardholders’ names that are the subject of the PCI DSS compliance list. Instead, they get only the expiration date and last four digits of the card number. This set of information doesn’t count as sensitive because a leak of that data won’t harm anyone. Developers need it to let users pay with their cards without entering credentials once again.
However, such convenience has its price. Stripe charges 2.9% + $0.30 per each successful transaction. On top of that, payment gateways don’t remove the responsibility from you in case something goes wrong. That’s why you should conduct research and find reliable PCI service providers with level 1 compliance like Stripe.
This guide explains all the details of integrating a payment gateway into your app.
What Do I Need to Be PCI Compliant: 7-Point Checklist
To become PCI DSS compliant, you need to go through the following steps:
1. Determine the compliance level - calculate how many transactions you conduct each year and compare that number to the requirements of the credit card companies you plan to support.
2. Map the cardholder data flow - identify all the details in the data path - including all the applications, systems, and people interacting. Your technical partner can help you with this step.
3. Fill out the Self-Assessment Questionnaire (SAQ) - this tool is used to validate PCI compliance and considers 12 essential requirements, which we'll discuss in detail later.
4. Complete the Attestation of Compliance (AOC) - this document varies depending on the PCI compliance level of your business and ensures that you fulfill every PCI compliance step.
5. Conduct a vulnerability scan - you must scan for security vulnerabilities and ensure you meet all standards. You can hire approved scanning vendors (ASVs) to do this.
6. Submit documents - AOC, SAQ, ASV reports, and other documents must be submitted to banks, credit card companies, and other organizations.
7. Monitoring - the PCI DSS compliance process involves constant monitoring as your business and its infrastructure may change throughout the year. You can hire a special security team to ensure you remain PCI compliant.
To simplify these processes, you can contact an experienced IT partner that will address all your answers to the PCI DSS compliance.
How to Implement PCI DSS Compliance: 12 Requirements to Follow
PCI DSS has some strict technical and organizational requirements. These requirements are logically organized into six groups. However, with the evolution of PCI DSS, these groups were divided into 12 sub-requirements. Let’s clear up that confusion right now.
Here’s the table of PCI DSS requirements and implementation details.
| Requirements | How to implement |
Build and maintain a secure systems |
|
| |
Protection of cardholder data |
|
| |
Vulnerability management program |
|
| |
Implement strong access control measures |
|
| |
| |
Regularly test and monitor your networks |
|
| |
Maintain an info security policy |
|
Let’s take a closer look at each sub-requirement individually.
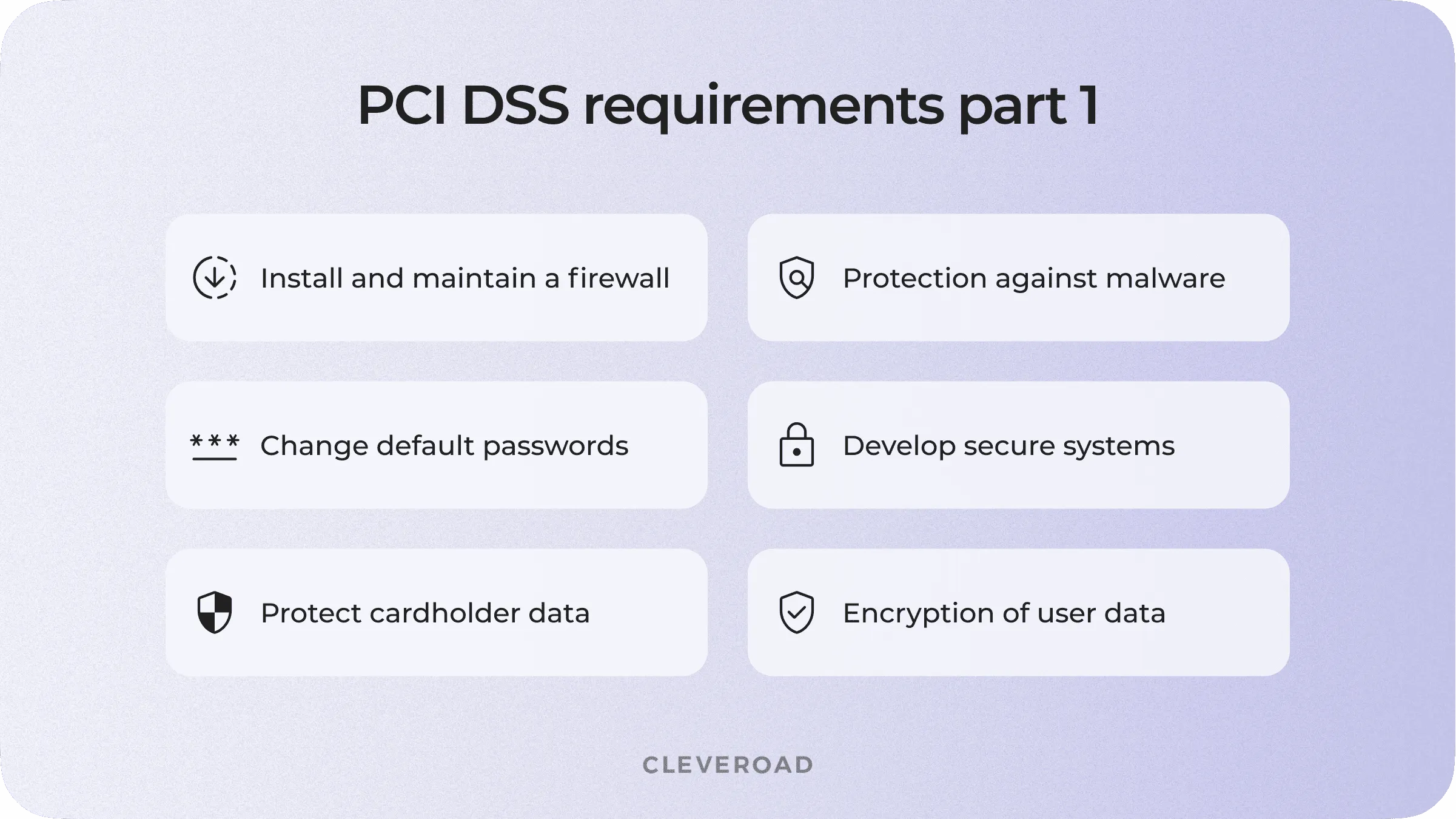
PCI DSS sub requirements
Install and maintain a firewall to protect cardholder data
A firewall is a security system that monitors incoming and outgoing traffic based on predefined rules. It serves as a barrier between internal networks and such external networks as the Internet. With the right adjustment, a firewall can detect atypical traffic and block it from getting to your network.
Change default passwords
Default credential vulnerability is one of the most common mistakes in cybersecurity. The first thing that hackers will try is to enter the “admin - admin” combination into the login form of your Wi-Fi network. How to comply with PCI DSS requirements? You have to make sure that not a single device in your network uses default credentials.
On top of that, don’t forget to change passwords on all new devices when scaling your network. PCI DSS regulations also recommend changing existing passwords every 90 days.
Protect cardholder data
If a hacker infiltrates your network and takes over the encrypted information without the access to cryptographic keys, all their efforts will be wasted in vain. The data will be unreadable, thus unusable to an intruder. Besides, you have to think of additional ways to mitigate the risks. They include:
- Avoid saving cardholder data unless you absolutely need it.
- Avoid sending sensitive data via emails and instant messages.
Encryption of user data in public networks
Sensitive information should be encrypted during transmission via public networks. Poorly protected wireless networks alongside outdated encryption and authentication protocols fall victim to fraudsters using various vulnerabilities to access personal data.
PCI DSS requirements oblige developers to use strong encryption protocols like TLS, IPSEC, and SSH for transmission over the Internet, cellular networks, and Bluetooth. The WPA2 security protocol is suitable for wireless networks, like Wi-Fi. Finally, all operational procedures for data encryption should be well-documented and known to all affected individuals.
Protection against malware and regular updates of antivirus software
Malware stands for malicious software. This concept includes viruses, worms, screen-locking ransomware, and other types of threats that get into the network during Internet-related business activities. Employees can face malware while emailing or using the Internet.
Antivirus software is one of the top priorities on the PCI DSS requirements checklist. It protects systems from malicious software by analyzing downloaded files and comparing them with examples of current and evolving malware. If antivirus software detects the threat, it blocks the file’s access to a computer and removes it.
Mind that the antivirus should be running without interruptions on all devices commonly affected by malicious software. If there’s a need to stop the antivirus, you should have a justified reason to do it. PCI DSS encryption standard requires managers to keep a record of every shutdown and track the access to the antivirus.
Develop and maintain secure systems and applications
Security vulnerabilities become the open door for hackers and fraudsters. All vendors should conduct testing and release security patches that plug up the holes in the app’s security system. Make sure that the system delivers and installs updates automatically on user devices.
One of the points of the PCI DSS compliance process is to teach developers how to use secure coding methods. They should avoid common coding vulnerabilities and treat the memory with sensitive data with caution. Besides, engineers should be familiar with secure coding guidelines.
Another advice to comply with PCI DSS policies is to hire so-called ‘White hats’. White hats are ethical hackers that search for vulnerabilities in your software. When hackers find a security issue in the system, they contact your support service and report about the problem. In return, companies offer financial compensation for each detected vulnerability. This practice is commonly accepted by large companies like Google, Amazon, and more.
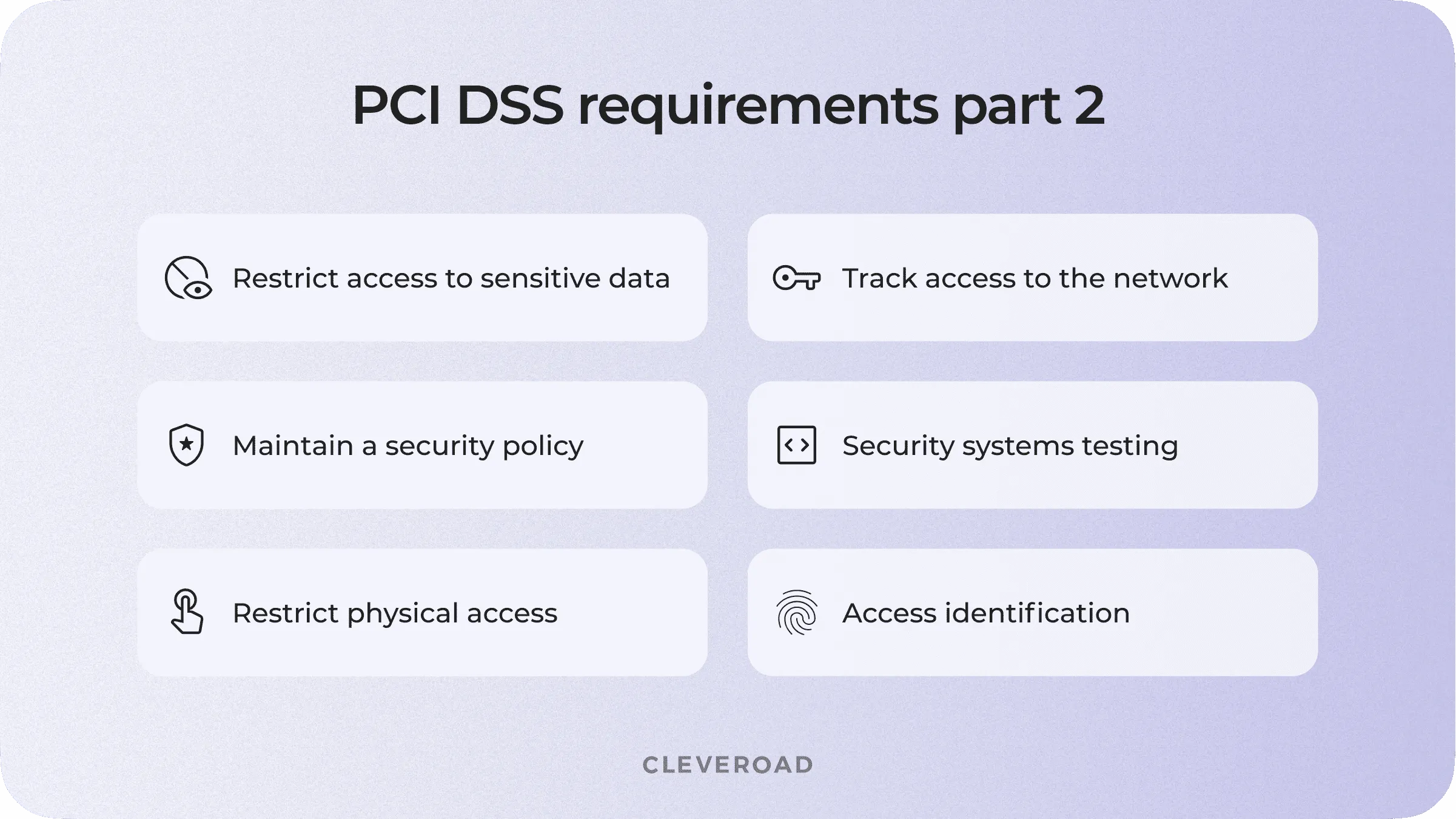
PCI DSS compliance list
Restrict access to cardholder data
Make sure that access to critical data is granted to authorized personnel only. To comply with this requirement, you have to define the access levels for each employee working with sensitive data. For example, you can use a need-to-know approach: only those individuals who need to know cardholder data for business operations must have access to this data. To achieve PCI compliance, the software should have pre-assigned roles for the personnel and provide information following these roles. Your system should also ask for documented approval when personnel access the data and automatically log off all users after a certain period of time.
Identifying and authenticating access to system components
A unique identification (ID) allows to track the actions of each individual in the system. A record-keeping via ID informs which users have worked with critical data.
That’s how those users responsible for suspicious activity can be traced.
Mind that PCI DSS audit requirements oblige app owners to disable inactive user accounts within 90 days. IDs are a perfect match for this case. Admins can track the date of the last action of each user. On top of that, they can revoke the session of every unauthorized user.
At this point, you also have to think about two-step verification for all devices that attempt to access the data outside of your network. This applies to your remote employees and all third-parties.
Restricting physical access to cardholder data
Physical access to sensitive data or systems that store this information allows intruders to make a copy of it physically. That’s why PCI DSS policies require video surveillance and entry controls in data centers. Collected data should be stored for at least three months.
Also, take care of procedures that help to identify onsite employees and visitors. ID badges are the most effective option that helps to identify and track employees in the data center. In case you need to let third-parties in (hardware vendors, outsourcing technical support), assign an employee that’ll escort visitors all time within.
Finally, if you’re working with devices that capture data via direct interaction with the card, protect them from tampering and substitution to become PCI compliant. Draw up a list of devices that includes:
- Model of the device
- The device’s location
- Serial number
It’s crucial to check devices’ surface for card skimmers and instruct your employees about possible risks. However, this PCI DSS requirement doesn’t apply to manual data-entry devices like keyboards.
Tracking and monitoring all access to the network
Tracking user activity is one of the main steps in preventing and detecting the reasons of data leakage. Logging every action lets you track and analyze patterns of user behavior and detect anomalies. If a breach happens, the successful logging system can assist in detecting the security breach.
To successfully get PCI compliant, you have to develop audit trails for all following components:
- Accesses to cardholder data
- All actions performed with admin or root rights
- Incorrect attempts of entering credentials
- All manipulations of identification and authentication mechanism
- Manipulation of the audit logs
- Creation or elimination of system-level objects
A well-built system that keeps a record of all listed events helps to reconstruct the attack script precisely and decide on further investigation steps.
Regular test of security systems
Before releasing your software, you have to test it for bugs and vulnerabilities. Every system component that is a subject to PCI DSS regulations should be tested after each update to ensure it still has the same security level in a different environment.
At this point, the main requirement is to perform an external vulnerability scan via an Approved Scanning Vendor (ASV) quarterly. Mind that ASV should be approved by the PCI Security Standards Council. However, you have to find an experienced software development company to make sure that you'll pass the scan successfully.
This article explains all the steps of hiring programmers for non-tech persons.
The PCI DSS standard also obliges you to conduct internal tests. Still, you can manage them on your own without an ASV vendor.
Maintain an information security policy for all personnel
Delivering information about security policy to employees is crucial for all PCI DSS compliant companies. First, you have to share the security policy among your employees and update them when the environment changes. You also have to conduct an annual PCI DSS risk assessment that identifies critical assets, threats, and vulnerabilities.
Additionally, all critical tech use policies should have a well-written documentation and define who’s responsible for what.
How to Implement PCI DSS Compliance on Mobile Devices
Even though the PCI DSS compliance process doesn’t depend on the type of device, mobile devices have individual vulnerabilities that have to be covered beforehand. Additional components, like NFC modules or cameras, create new opportunities for exploits and breaches. Let’s single out each of them and figure out how to deal with these issues.
Cellular Network
Alongside standard communication methods, mobile devices use cellular technologies (CDMA, 4G, 5G). However, these networks can be much more beneficial for hackers than internal networks of a company.
When we’re talking about the wireless network in your data center, hackers can DDoS attack your router to force sysadmin to make a hard reset. With a hard reset, the router’s credentials are reset to default. That’s how fraudsters can get access to all the traffic in your network.
Solution: A correctly adjusted network (in accordance with PCI DSS) will allow you to prevent all attack attempts.
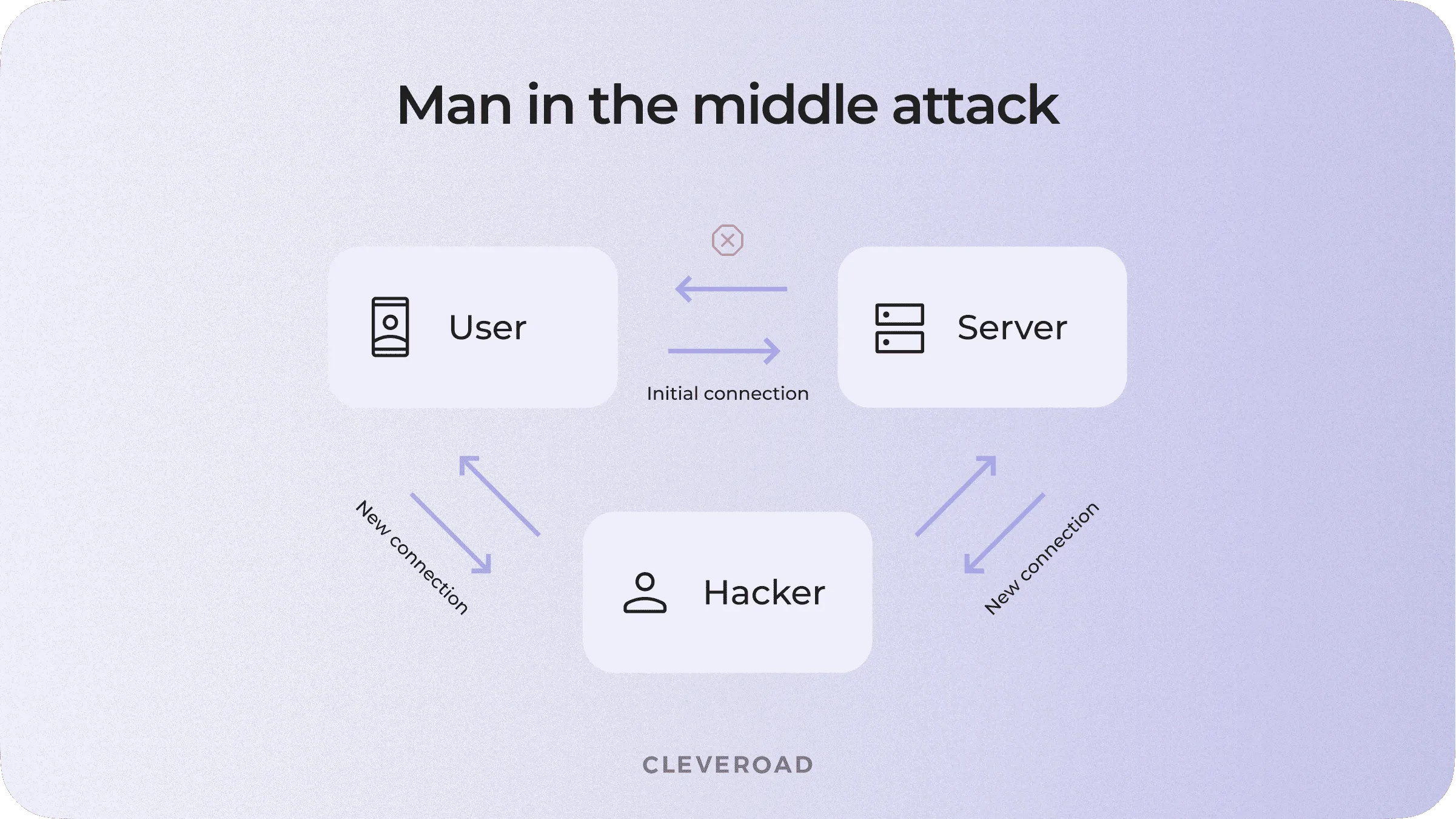
How does 'man in the middle attack' works?
As for mobile networks, hackers use TDoS (telephony denial of service) attacks. This type of attack allows attackers to infiltrate on call between two parties. In case you have technical support that solves transaction issues, hackers can interrupt the call and act as if they are technical support officers. This type of attack lets fraudsters steal sensitive data directly from the customer. Obviously, this situation is unacceptable according to PCI DSS compliance requirements.
Solution: Your software solutions must include features enabling you to warn your users not to disclose their credit card data to other persons.
Camera
Smartphone cameras become the third eye in the hands of a professional hacker. Let’s begin with a simple example.
In case you’re using QR codes in the data center’s workflow, an infiltrated person can swap them for harmful codes that may snatch the data from the employee’s device. For example, a QR code leads to a web form that asks for the employee’s credentials. If the fraudster manages to substitute the code for his own, after the scan, they will receive the employee’s credentials to grant access to the internal network.
Another case is malware that makes photos and records video without the owner’s permission. This vulnerability may lead to leaks of both written and oral information. On top of that, attackers get access to the photo's geolocation and gain full access to the user’s media files. T
Solution: Consider your employees' training to increase their awareness of the security policy and the need to use antivirus software on their mobile devices — following PCI DSS requirements.
What Can Cleveroad Do For You For Achieving PCI DSS Compliance?
Cleveroad is a professional software development company with 10+ years of experience. Our team builds digital solutions for small and medium-sized businesses, startups, and enterprises in various domains, including FinTech, Logistics, Healthcare, Media and others.
Our team has practical experience in creating software solutions compliant with PCI DSS, GDPR, ISO 27001, and other essential security regulations. Our software engineers have an in-depth knowledge of all up-to-date vulnerabilities and breaching techniques. We’ve built more than 170 successful projects and worked with payment systems of different complexity.
Get a PCI DSS compliant software
Talk to our experienced Solution Architect on how to make a robust app to meet security standards
To become PCI DSS compliant you have to follow 12 PCI DSS requirements, get accreditation from Qualified Security Assessor, and conduct quaterly network scans for vulnerabilities.
Being PCI DSS compliant means that it's safe to transmit credit card data via your software.
- Install and maintain a firewall to protect cardholder data
- Change default system passwords and passwords for network equipment
- Protect cardholder data. Implementation of hashing, encrypting, and truncation methods
- Encrypt cardholder data while it’s transmitted over public networks
- Regular updates of anti-virus software and strong security measures against malware
- Develop and maintain secure systems and applications
- Grant access to cardholder data only to authorized individuals
- Track and log all access attempts to sensitive data
- Restrict physical access to cardholder data
- Track and monitor all attempts to access network resources and cardholder data
- Regularly test security systems and processes
- Maintain a policy that addresses information security for all personnel
PCI DSS stands for Payment Card Industry Data Security Standard. PCI DSS is a full-fledged protocol that sets high standards of handling sensitive data.
Failing PCI DSS compliance means that the software has vulnerabilities and may lead to data leaks. In case users' personal data gets exposed, the app owner will be fined. Fines range from $5,000 to $100,000 per month depending on the business size and the type of non-compliance.
There are four levels of PCI DSS compliance. Depending on the number of annual transactions, PCI DSS protocol sets requirements for companies.
- Level 1 — over 6 million of Visa or Mastercard transactions per year or 2.5 million transactions of American Express per year. Each year a Qualified Security Assessor conducts an audit and writes an Annual Report on Compliance. Besides, an approved company conducts a quarterly network scan to detect vulnerabilities.
- Level 2 — between 1 and 6 million transactions per year. This level of compliance obliges companies to conduct an annual PCI DSS assessment. Annual ASV scanning is also required.
- Level 3 — between 20,000 and 1 million transactions per year. The overall requirements are similar to those for level 2.
- Level 4 — under 20,000 transactions. The overall requirements are similar to those for levels 2 and 3.

Evgeniy Altynpara is a CTO and member of the Forbes Councils’ community of tech professionals. He is an expert in software development and technological entrepreneurship and has 10+years of experience in digital transformation consulting in Healthcare, FinTech, Supply Chain and Logistics
Give us your impressions about this article
Give us your impressions about this article
Comments
4 commentsInformative and on-point article. As a person who went through the PCI DSS assessment, I suggest everyone find an experienced sysadmin. Setting up a network on your own is a tough challenge.
Superb content! Keep on keeping on!
I love your content. I think that going with third-party payment gateways is much easier and can spare your nerves. Still, Those interested in custom payment systems can learn a lot from this post.
Thanks for an extensive guide on PCI DSS. You've explained all requirements in plain language