Android as a Bodyguard or What Keeps Your Applications Secure?
Updated 12 Jan 2023
10 Min
2967 Views
It is a funny thing, you know. Only 5-7 years ago there was a kind of trend for the installation of security devices. Nowadays, we can observe similar tendencies but in the IT technology field. You can ask 'what are you getting at?'. The answer is quite simple. It is unnecessary for modern fraud even to leave his house in order to steal money from your credit card.
Half a decade ago everybody was afraid of a burglar breaking into an apartment, but now this burglar has become much smarter, got two higher educations and additional skills in hacking devices.
Take a look at your calendar. It is 2016 already. It is high time not only for traps and security systems installation but mobile application security as well.
What has happened with the green robot? Get the latest news from Google I/O 2016.
Remember how many scandals related to digital security have happened this year? A lot! That is why the entire industry is striving to invest money in the protection of their products. Moreover, they try to draw consumer's attention to their efforts in making secure software. This way, trying to ensure users that it is absolutely safe to use their software.
In this article, we are going to discuss the security aspects in Android OS.
Mobile App and Data Security in Android
Android for every life situation
I think that everybody is aware of this OS. It is not a secret that it is the world's most popular mobile operating system at the moment. Speaking about the Android ecosystem we can refer to Android OS itself, Android Wear (OS for smartwatches), Android Auto (OS for car trip computers) and Android TV (OS for smart TVs).
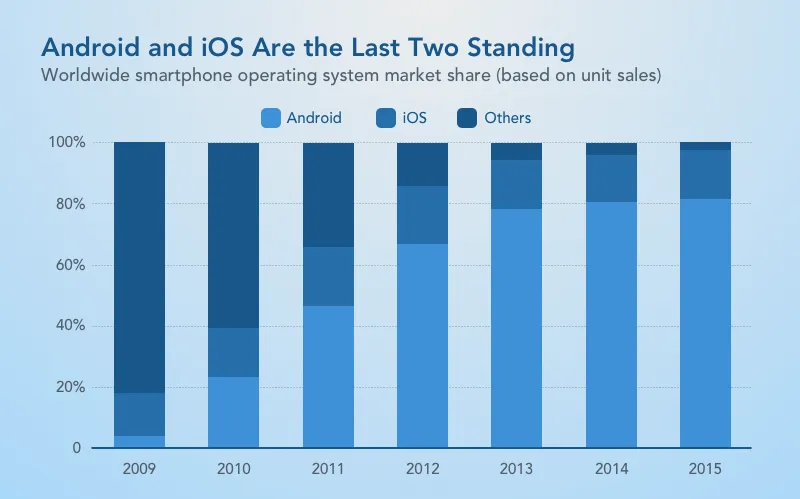
Android users in comparison with iOS (Source: Statista)
As you can see, Android dominates the market. First of all, it is due to the diversity of supported devices and the moderate prices for them.
The importance of an app's security
No one wants his information to be stolen. Android developers should understand the importance of security in every application. However, there is a list of apps which are especially in need of protection.
So, we can refer here to social networks, messengers, cloud storages, apps for work with documents and so on. Such apps contain our personal chats, photos, notes, documents etc. That's why it is important to provide strong security systems there.
I will not load you down with all these complicated protocol names or the defence layers that are used during your app's development. I just want to emphasize that all these serious software features will not protect your information from one of your nearest and dearest. Sometimes, the person can guess or accidentally find your password out.
We think that the most effective way to protect user's data is a fingerprint scanner. This feature firstly came to iOS. Then, smartphone manufacturers have gradually started introducing their own variants of this technology. And IT developers began using it in their software. Nowadays, this feature is supported by Dropbox, Evernote, WhatsApp and other applications. Unfortunately, it is not a cross platform solution. While separate iOS applications support this feature - Android does not and vice versa.
Google is trying to catch up with modern trends in both software and technical components of their devices. This way, providing security for user's apps and data.
Mobile app and data security in Android
At Cleveroad, during mobile development, we follow up-to-date security guidelines provided by Google company. It is a very important step for producing top-notch software. Let me introduce these principles.
Storing your app user's data
Probably the most important thing in digital security is the way of storing your data. Whether it is accessible to other apps or not. There are two ways of saving data on your device.
Internal storage
A file created in the internal storage while using a certain application is hereinafter unavailable for use beyond this app. Let me give you Google's example for this technology. Imagine a simple sandbox. The sand inside of it - is your personal information. This sand cannot pour out of it because of the walls. In the same way, your information from one app cannot be accessible by another one because every single app is stored in it's own virtual sandbox. So, they are isolated from each other.
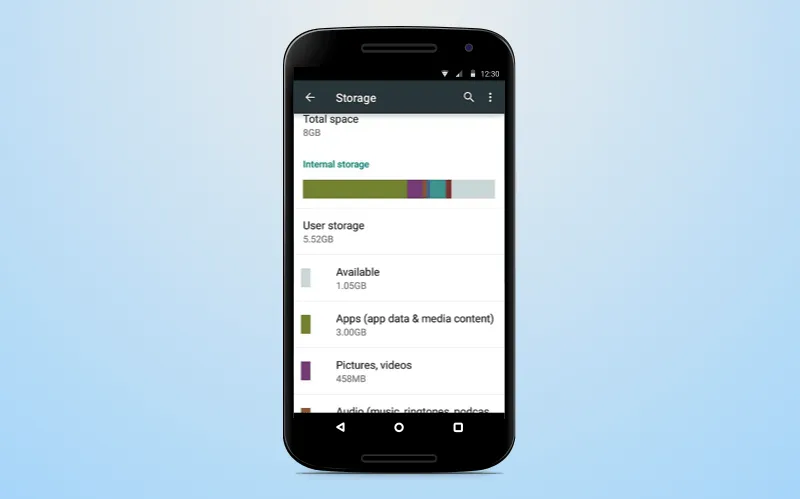
Android internal storage
For additional protection, the user can set an encryption with the help of a password. This password is not directly stored in the device's memory.
When this encryption is enabled it protects the key elements of the OS.
External storage
We do not recommend saving your app user's confidential information on SD Cards as they can be removed by users or modified by any application. Nevertheless, you can restrict the access to SD Cards in your application.
Permission in Android OS
Sandbox systems demand user's permission for interaction between apps. So, if you want your Android app to be friendly, coders should implement this function using a sandbox system.
Permission is almost the main security feature in this OS. It makes sure that apps do not collect your data and do not use too many resources. This system provides security to Android application security and your user's data as well. Moreover, all the apps and processes are restricted and do not have unreasonable access to the system level.
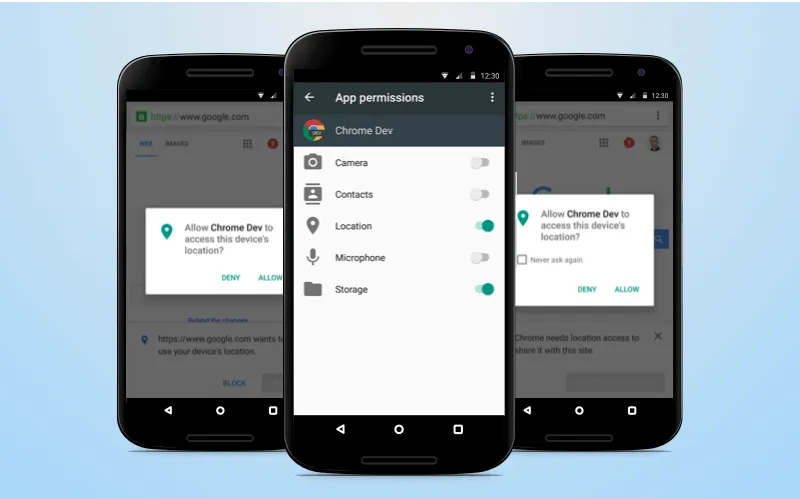
The way permission is realised in Android
Networking and data transferring
The most dangerous process in a modern digital world is the connection to the Internet. Practically, all cyber crimes are committed through the Internet connection. In order to secure your web traffic, Google uses HTTPS protocol. This protocol provides Android mobile security with protection for privacy and integrity of the exchanged data.
Google also gives you an opportunity to use an SMS method of data transferring to users (for example, the password recovering PIN). This kind of notification became possible with the help of Google Cloud Messaging (GCM). For adding this feature to your app, the coder should be competent in GCM service capabilities.
We cannot omit the fact of Google Play safety. For clarity, let's look at the stages that apps should pass before being installed from Google Play.
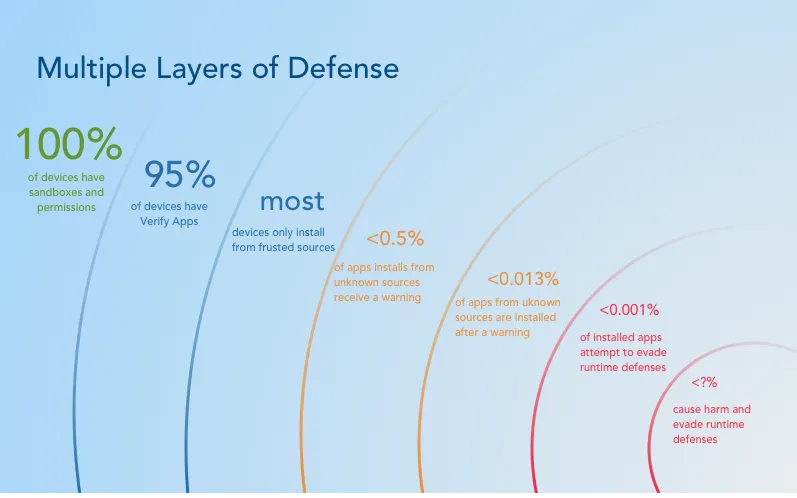
Layers of defense in Google Play
The app must get through Google's 'Verify Apps' security feature helping to check for an APK on malware occurrence. Then, the app is sandboxed and restricted to the permission granted to it. Finally, Android conducts a recheck of the application every time it is run.
Built-in security
Android is Linux-based OS. It means a wide variety of built-in security mechanisms. Android supports such protocols as AES and RSA for encryption, Digital Signature Standard (DSS) for authentication etc. All these protocols are provided with one single purpose - to ensure mobile security in Android.
Also, this OS has a safety mode which allows disabling all the extra processes in order to find and remove the problem.
The perfect password
Probably, the only thing modern hackers still cannot overpass is a fingerprint password. It is a very convenient way of keeping your user's files secure. In addition, there is no need for memorizing all these annoying and long passwords. Your user's password is always on hand. It makes your application more convenient.
This feature came to Android quite recently. IT companies all around the world have immediately started updating their products in order to add the support of this function. As we can see, it is really important to keep up with the times, especially in such a rapidly developing industry. However, you need a professional team to make the grade.
Android 7.0 is coming
We have already discussed the main security features presented in previous Android versions. But what about upcoming Android Nougat and it's security of mobile applications and data?

Android Nougat interface
New way of booting and stronger encryption
Now, there is no need for entering the security code everytime after the reboot of an encrypted device. Google has simplified this process. However, it remains as safe as before. The point is that applications which do not require access to user's data (such as an alarm and phone) will work on encrypted phones without any passwords. For using functions containing certain data (e.g. a phone list) - the user should enter his password.
Complicated app interaction
In Nougat, the company focused their attention on permission sharing between apps. In previous versions of the operating system, apps were able to share user's permission with each other more easily than in the upcoming update. Apps with admin permission will no longer demand that the user enters a PIN or password for uninstalling them. This feature takes Android to a new level of mobile apps and data security.
'Seamless' update feature
Have you ever needed your phone during it's updating process? Exactly! Every time your phone is unavailable, an urgent necessity to use it appears. Probably, Google's top managers have also faced this problem. So, they decided to introduce the seamless update feature.
What does it mean? This feature allows using the phone during the updating process. The updated files are being installed on a separate device partition so that users can continue working. After the installation process, users should reboot their devices and the new OS version will be available.
Unfortunately, this feature will be available only for owners of new devices.
The architecture of Android security systems
From the graph below we can see that companies get great income from their security systems development. Google is not an exception.
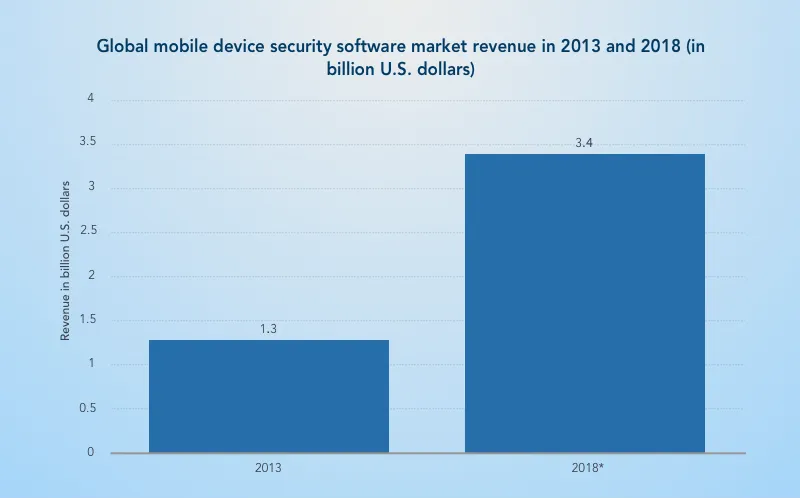
Security software revenue (Source: Statista)
To make everything abovesaid clear, let's make a list of Android's security points.
- Protection of already installed applications and user data
- Protection of system resources including the network connection
- Complete app isolation
It seems to be too simple. However, these protection layers provide maximum security in OS interaction with your data.
Now, let's see how Google manages to obtain such security levels.
- High-security system level provided by Linux kernel
- Applications are isolated with the help of sandboxes
- Protected interprocess communication
- Processes having an impact on OS security are solved personally by a user
Google has introduced not only a built-in security system but also a wide range of online services which safeguard your user's device providing more detailed Android mobile security.
- Google play. This service is the most visited among the Android owners. We have already mentioned the security layers there. So, you can download apps from it without any fear
- Android updates. I think that the main function of this service is understood. It is aimed at keeping your software up-to-date. Built-in defense protocols do not allow collection of users' data while updating
- Application services are used for access to the cloud's capabilities such as backing up and push messaging
Find out the secrets of software development. Read our article related to software development methodologies
- Verify apps. Warn the user about installing harmful apps or even block them. Also, the service constantly scans already installed applications and reports to the user about the threats
- SafetyNet. The system aimed at the detection of privacy intrusion. It helps to detect and fix security problems
- Android device Manager. A web and Android app which helps in detecting lost smartphones
You've probably never thought that such usual things in the digital world are under such complicated layers of defense.
Summarizing
It is worth noting that Google remains the leader in the digital world. It produces a high-quality products which are loved by millions of people around the world.
All their operating systems are unique. In good hands, it is possible to create a fascinating software product.
Do you want to hire an Android application development company like Cleveroad? Our professional team will be glad to help you with this difficult task. Be it a project connected with Android Wear, basic Android or whatever. We will do anything to satisfy you with the result.
By the way, you can see our work in Cleveroad portfolio and you may follow us on Dribbble and Behance. Also, take a look at our video related to this topic.

Evgeniy Altynpara is a CTO and member of the Forbes Councils’ community of tech professionals. He is an expert in software development and technological entrepreneurship and has 10+years of experience in digital transformation consulting in Healthcare, FinTech, Supply Chain and Logistics
Give us your impressions about this article
Give us your impressions about this article