iOS App Development Services
Building and delivering iOS apps on the basis of native programming languages like Swift and Objective-C to provide a superior performance.



Core industry expertise
We also have customers in these domains
Technologies for advanced iOS apps
Big Data
- Big data architecture design
- Apache Spark and Hadoop
- HDFS, Hive, Pig, Impala, Oozie
- EMR, Redshift
Media Expertise
- Live Streaming and OTT delivery
- Video Processing
- Content Distribution Networks
- Web RTC, FFMPEG, Wowza, DRM
Apple Resources
- Frameworks: CarPlay, 3D Touch, Adaptivity
- App Services: Apple Pay, HealthKit, HomeKit, CloudKit
- Media and Web: MapKit JS, Live Photos, AVFoundation
Computer vision
- Image processing
- Deep Learning OCR: Keras, Supervisely
- Face recognition: Eigenfaces, LEM, Facial morphology analysis
- Face Detection: HOG, SVM
- OpenCV, Kairos, Luxand Face
ML & AI
- Self-taught algorithms recognize user activities
- Artificial neural networks
- NLP software development
- Azure ML, Google Cloud Prediction TensorFlow
IoT Expertise
- Protocols: NFC, Wi-Fi, Bluetooth, LPWAN, IPv6 over LoWPAN
- Communication Security (TLS, DTLS) and Data Encryption
- Artik module, Raspberry Pi, Arduino
- AWS: Lambda, Kinesis, S3, SageMaker, Sumerian
Case Studies of Successfully Delivered iOS Projects
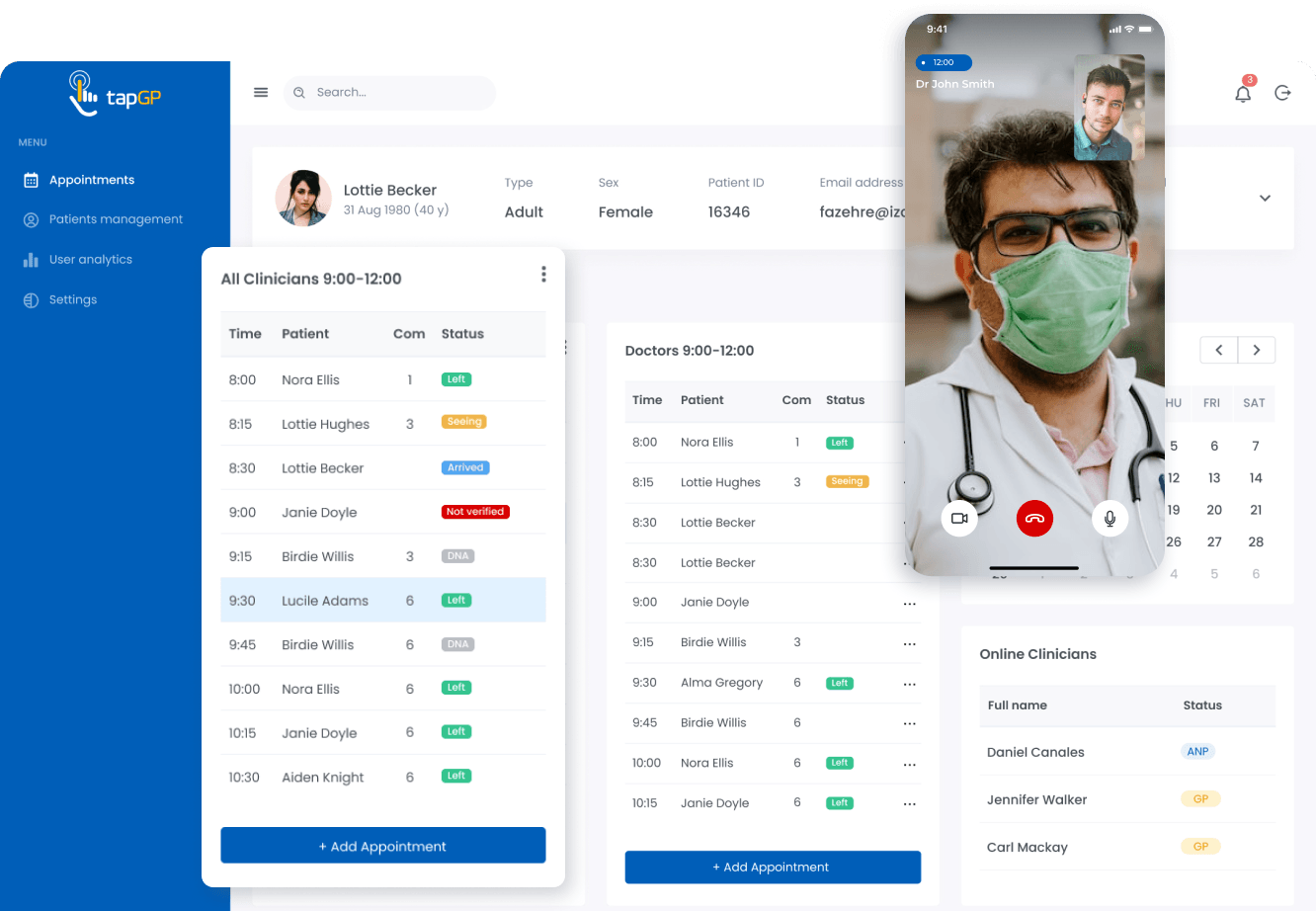
Challenges solved:
- Development of the SaaS for providing and receiving telecare services
- Providing 24/7 online access to video and audio consultations of general practitioners and clinicians
- Creation of an online appointment booking functionality
- Compliance with the requirements of GDPR and UK healthcare regulators (CQC and MHRA)
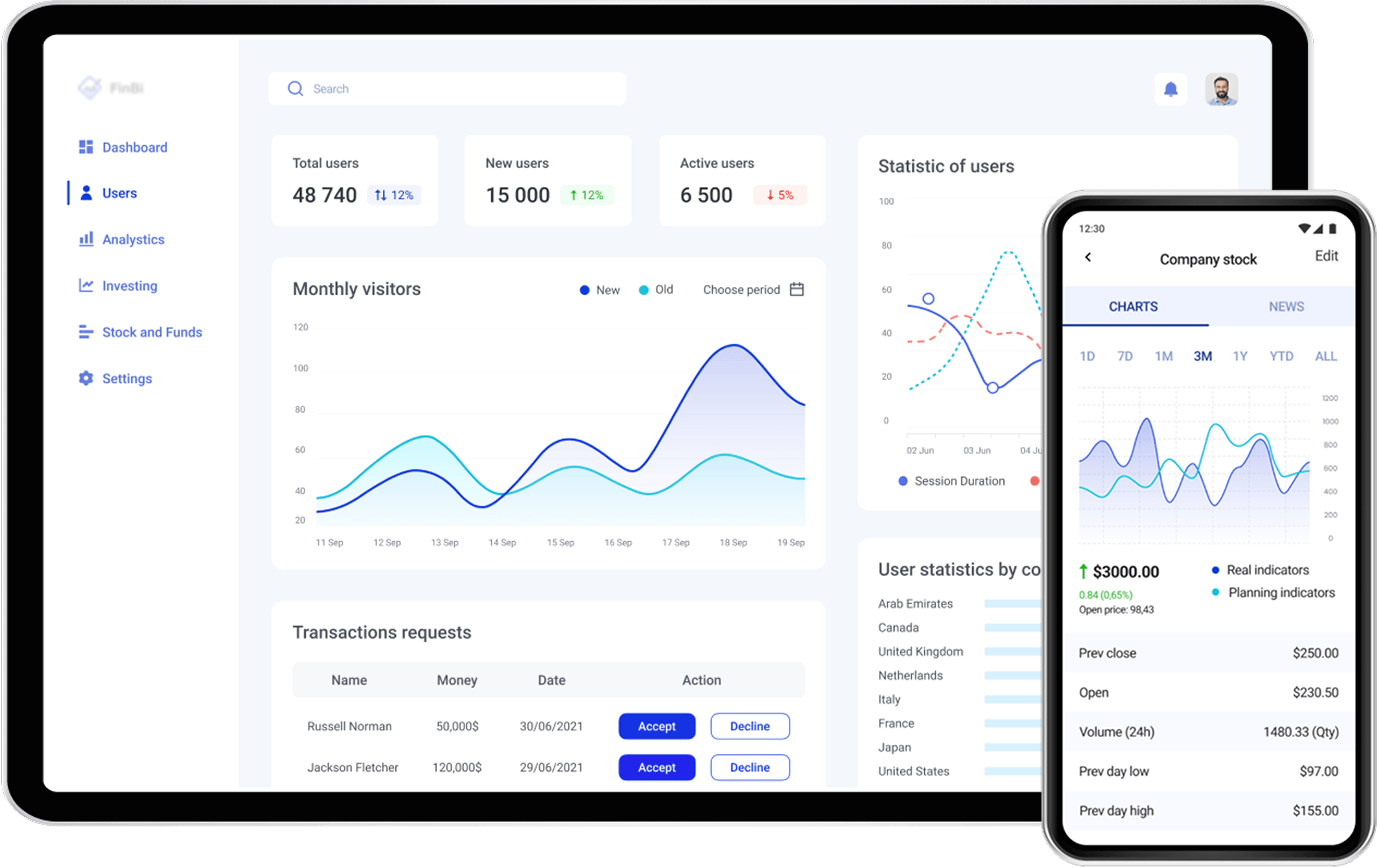
Challenges solved:
- A micro-investing application is built from scratch
- The solution is compliant with local FinTech legislation (namely SAMA)
- Any sensitive data is kept black-boxed and securely protected
- KYC verification with liveness detection is implemented
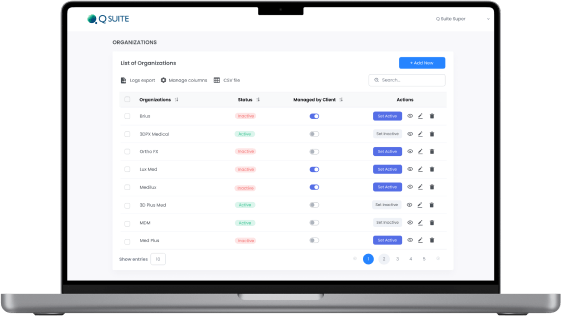
Challenges solved:
- Development of a Quality Management System (eQMS) from scratch
- Automation and UX improvement of document flow and processes of FDA/ISO certification
- Creation of a B2B SaaS to check compliance to FDA 21 CFR 820, 21 CFR 11 and conformance to ISO 13485:2016 and MDSAP
Industry Contribution Awards
70 Reviews on Clutch
4.9

Award
Clutch 1000 Service Providers, 2024 Global

Award
Clutch Spring Award, 2025 Global

Ranking
Top AI Company,
2025 Award

Ranking
Top Software Developers, 2025 Award

Ranking
Top Web Developers, 2025 Award

Ranking
Top Staff Augmentation Company US, 2025 Award
Technology stack for iOS platform
Our iOS app developers keep up with the latest tech trends and sharpen their expertise to deliver software solutions for a rapidly evolving market.
Languages
Databases
FRP and networking
CI/CD
Swift
Swift is a robust programming language backed by Apple that allows creating top-notch and fast applications for all Apple operating systems. Safety, simplicity, and permanent performance enhancements make iOS app development with Swift an ideal solution for building iOS apps of any complexity.
Certifications

ISO 27001
Information Security Management System

ISO 9001
Quality Management Systems

AWS
Select Tier Partner

AWS
Solution Architect, Associate

Scrum Alliance
Advanced Certified, Scrum Product Owner

AWS
SysOps Administrator, Associate
Our Clients Say About Us

CTO at NURSING
"The team is very organized, communicative, and proactive. They keep the project on track and provide excellent suggestions to improve the product."
iOS app development insights
If you want to know how long it takes to build your app, please contact our Business Analysts.
We also offer extended maintenance periods that ensure you being covered after the project release.
- Business analysis. We gather and analyze all the project requirements and document them.
- UI/UX design. Create wireframes, design the app screen by screen, and make a prototype.
- Development. Build custom iOS apps using programming languages like Swift and Objective-C.
- Release. Publish apps on the App Store.
- Maintenance. Support or enhance existing products (if requested).
- Expertise: portfolio, industries they work in, how long they’ve been working for.
- Reviews: on Clutch, GoodFirms, or similar services.
- Tech stack: it should include programming languages Objective-C and Swift, app-building tools (Fabric, Fastlane), databases (CoreData, Realm, Firebase), and so on.
- Business analysis
- UI/UX design
- Development
- Release
- Maintenance (if requested)