Sheltering Medical Data: A Provider’s Guide to Healthcare Data Security
Updated 22 Aug 2023
17 Min
768 Views
Healthcare institutions process a huge amount of sensitive patient information. This invaluable database attracts the attention of attackers, and cyberattacks on medical facilities are becoming increasingly common.The subject of health data security and processing cannot be underestimated by any up-to-date business which strives to stay relevant and competitive.
Let’s explore the challenges healthcare facilities face as to data protection and present the security measures to protect sensitive patient information.
What Is Data Security in Healthcare: Quick Overview
Data security in healthcare refers to the measures and practices implemented to protect sensitive patient information, known as electronic protected health information (e-PHI). It involves ensuring the confidentiality, integrity, and availability of this data to prevent unauthorized access, disclosure, or alteration.
Micky Tripathi
National Coordinator for Health Information Technology
Securing healthcare data is a shared responsibility that requires collaboration among healthcare organizations, technology providers, and policymakers to create a culture of data protection.
Types of data to be protected
Various types of data in healthcare settings need to be safeguarded to maintain patient privacy and prevent unauthorized access. Within the definition of data security in healthcare, they include:
- Personal Identifiable Information (PII). This includes patient names, addresses, social security numbers, and contact details.
- Medical records. Electronic health records (EHRs), medical histories, test results, diagnoses, and treatment plans.
- Payment information. Credit card details, insurance information, and billing records.
- Research data. Clinical trial information, genomic data, and other sensitive research-related data.
General rules for data security in healthcare
Healthcare organizations must adhere to the security requirements outlined by the Health Insurance Portability and Accountability Act (HIPAA) regulations. The HIPAA Security Rule mandates covered entities to maintain reasonable and appropriate safeguards for protecting e-PHI. They imply:
- Procuring the privacy, integrity, and availability of all e-PHI created, obtained, retained, or processed.
- Recognizing and protecting against reasonably anticipated threats to the security or integrity of the information.
- Protecting against reasonably anticipated, impermissible uses or disclosures of e-PHI.
- Assuring compliance by their team through training, policies, and procedures.
- Compliance with these regulations is crucial for healthcare organizations to mitigate the risks of data breaches, maintain patient trust, and avoid legal and financial consequences.
Factors risking data security
Several factors pose risks to data security in healthcare organizations. It is essential for healthcare organizations to be aware of these factors and take appropriate measures to mitigate them:
- Applying obsolete/legacy systems. Operating on outdated or legacy systems increases the vulnerability to security breaches as these systems may lack necessary security updates and patches.
- Email scams with malware. Phishing attacks and email scams can trick employees into clicking on malicious links or attachments, leading to malware infiltration and unauthorized access to sensitive data.
- Internal workers, contractors, and providers. Insiders within the healthcare organization, including employees, contractors, and vendors, can pose a risk to data security. This may involve sharing private data with outside parties, falling victim to malware schemes, or intentionally stealing data for personal use.
- Unprotected wireless Network security. Weak or insufficiently secured wireless networks provide opportunities for hackers to intercept data transmissions, gain unauthorized access to the network, and compromise sensitive information.
- Absence of solid passwords. Weak or inadequate password management practices make it easier for unauthorized individuals to gain access to systems and sensitive data.
- No guidance in data security healthcare practices. Insufficient training and awareness among employees about data security practices can lead to inadvertent security breaches, such as improper handling of data, falling for social engineering attacks, or failing to recognize potential threats.
- Negligence to maintain data protection. Neglecting basic security measures, such as regular data backups, encryption, and secure disposal of physical media, can leave data vulnerable to breaches, theft, or accidental exposure.
Each medical business should address these risk factors through proactive measures, thus enhancing its data security and protecting sensitive patient information from potential threats.
Discover how Cleveroad healthcare software development company can help your medical business
Why is Data Security Important in Healthcare and Must Be Prioritized
Data security in healthcare is of paramount importance as breaches and loss of data can have severe consequences for healthcare businesses.
Statistics show that security attacks in the medical sector have serious financial consequences for medical businesses:
- According to a study by IBM Security, the cost of the average healthcare security breach incident is about $7.13 million. This includes the cost of incident response, recovery, regulatory fines, and lost revenue due to reduced patient and business partner confidence.
- A report by the same source states that the average total loss from a healthcare data breach is about $10.10 million in 2022. This includes the costs of attack prevention, response, recovery, loss of business, and a diminished reputation.
- Another study by HelpNetSecurity found that 92% of pharmaceutical organizations have experienced at least one data breach in the past three years. As a result of data security healthcare breaches, 64% of the organizations have lost patients, 29% have experienced serious revenue reductions, and 27% have experienced negative consequences for their reputations.
- According to the National Institutes of Health, the average amount of fines imposed on healthcare organizations because of HIPAA violations is about $1.5 million. However, fines can increase significantly depending on the severity of the breach and the level of non-compliance with security requirements.
These statistics underscore the importance of data security in healthcare and the need for appropriate measures to prevent security attacks. Data loss and the financial consequences can seriously impact business reputation, patient trust, and the sustainability of medical businesses.

Administrative healthcare data security measures
Let's explore the significance of protecting healthcare data and the potential risks involved.
- Financial implications. Data breaches in healthcare can incur substantial financial costs. According to statistics, healthcare data breaches cost organizations an average of millions of dollars in damages, including expenses for incident response, regulatory penalties, legal actions, and reputation damage. Prioritizing data security is crucial to mitigate these financial risks.
- Privacy and confidentiality. Healthcare data, such as electronic health records (EHRs), contains highly sensitive information about patients' medical conditions, treatments, and personal details. This data must be protected to maintain patient privacy and confidentiality. Breaches in privacy can not only compromise the trust between patients and healthcare providers but also have legal and ethical implications.
- Security of medical data. Medical data stored in digital files, databases, and other records contain vital information that hackers can exploit. Breached data security healthcare can lead to identity theft, insurance fraud, or misuse of sensitive health information. Ensuring the security of medical data is essential for safeguarding patients' health and well-being.
- Financial details protection. The healthcare sector often handlesthe financial data of patients, including payment information and insurance details. In the event of a successful cyber-attack, criminals can gain unauthorized access to this financial data, leading to potential financial theft or fraud. Protecting financial data is crucial to prevent financial losses for patients, healthcare providers, and institutions.
- Personal details safety. Healthcare databases store personal information such as addresses, contact numbers, and identification numbers. If this data falls into the wrong hands, patients may become targets of blackmailers or stalkers. Attackers can exploit personal data to gain unauthorized access to social media accounts, bank accounts or commit other forms of cybercrimes. Prioritizing data security helps prevent such malicious activities.
By prioritizing data security in healthcare, organizations can mitigate financial risks, preserve patient data security and privacy, and protect sensitive medical, financial, and personal information. Implementing robust security measures, adopting best practices, and complying with regulatory requirements can safeguard healthcare data and maintain the trust of patients and stakeholders.
How to Secure Healthcare Data: 8 Proven Approaches to Data Protection
Securing healthcare data is crucial to protect patient privacy and prevent unauthorized access. Here are eight proven approaches defining how to secure healthcare data:
1. Risk assessment and threat identification
Conduct regular risk assessments to identify potential vulnerabilities and threats to healthcare data. This helps in prioritizing security measures and implementing appropriate safeguards.
2. Data encryption and access control
Encrypt sensitive data, both at rest and in transit, to protect it from unauthorized access. Implement strong access controls, including role-based access and multifactor authentication, to ensure that only authorized individuals can access the data.
3. Compliance with regulatory requirements
Adhere to industry-specific regulations such as HIPAA, GDPR, and local data protection laws. Implement the necessary technical and administrative measures to comply with these regulations and protect patient data.
4. Personnel education and awareness
Provide regular training and education to staff on data security healthcare best practices. Ensure that employees understand their roles and responsibilities in protecting patient data and are aware of common security risks, such as phishing attacks.
5. Secure network architecture
Implement a secure network infrastructure with firewalls, intrusion detection systems, and regular security updates. Segment networks to restrict access and prevent lateral movement of medical data security threats.
6. Backup and disaster recovery planning
Regularly backup healthcare data and develop a comprehensive disaster recovery plan. This ensures data can be recovered in case of system failures, natural disasters, or cyber-attacks.
7. Secure mobile devices
Establish secure healthcare data policies and enforce measures for mobile devices used in medical settings. This includes device encryption, remote wiping capabilities, and strong passwords or biometric authentication.
8. Collaborating with an experienced technical provider
Partner with a reputable and experienced technical provider specializing in healthcare data security. They can offer expertise, tools, and services to enhance data protection and keep up with evolving security threats.
By implementing these health care data security approaches, healthcare organizations can significantly strengthen their data security posture and mitigate the risk of data breaches, ensuring the confidentiality, integrity, and availability of sensitive medical information.
Key Health Data Security Standards to Follow
Healthcare organizations need to adhere to specific data security standards to protect sensitive patient information. Here are some prominent health data security standards applicable in different countries:
- HIPAA (Health Insurance Portability and Accountability Act). HIPAA sets the standard for protecting sensitive patient data in the United States. It mandates security and privacy measures for healthcare providers, health plans, and clearinghouses, emphasizing the importance of administrative, technical, and physical safeguards.
- PIPEDA (Personal Information Protection and Electronic Documents Act). This guideline is the Canadian data protection law that governs the collection, use, and disclosure of personal information in the private sector. It includes provisions for safeguarding health data and requires organizations to obtain consent for its collection and use.
- GDPR (General Data Protection Regulation). This is a comprehensive data security healthcare regulation applicable in the European Union (EU) and the European Economic Area (EEA). It applies to healthcare organizations processing personal data of EU/EEA residents, emphasizing consent, data minimization, security measures, and individuals' rights.
- HITRUST (Health Information Trust Alliance). This regulation is a widely adopted framework that provides a comprehensive set of controls for managing and protecting health information. It combines various regulations, standards, and best practices, including HIPAA, to establish a robust security and privacy framework.
- NIST (National Institute of Standards and Technology). NIST develops and promotes cybersecurity standards and guidelines in the United States. Its publications, such as the NIST Cybersecurity Framework and Special Publications (e.g., SP 800-53), provide valuable guidance for securing healthcare data and systems.
- ISO 27001 (International Organization for Standardization). This law is an international standard for information security management systems. It provides a systematic approach to managing sensitive information, including health data and implementing controls to mitigate risks.
- PCI DSS (Payment Card Industry Data Security Standard). While primarily focused on payment card data security, PCI DSS is relevant to healthcare organizations that handle payment transactions. It outlines requirements for securing payment card information, protecting against breaches, and maintaining a secure network infrastructure.
Take a look at our checklist for HIPAA compliance in software development
As for the Asia-Pacific region, health data security and privacy regulations vary across different countries. For example, in China, the Cyber Security Law (CSL), Data Security Law (DSL), and the Personal Information Protection Law (PIPL) govern the collection, management, and exchange of personal health information. These laws impose restrictions on data manipulation, require patient consent, and enforce scrutiny for cross-border data transfers.
In India, the Personal Data Protection Bill is currently under consideration to establish comprehensive data protection regulations.
Healthcare organizations operating in the Asia-Pacific region should be aware of the specific data privacy laws and regulations in each country they operate in to ensure compliance and protect patient data according to local requirements.
By aligning with these standards and frameworks, organizations can establish a strong foundation for data security in health, ensuring compliance with relevant regulations and fostering trust among patients and stakeholders. It is crucial to consult the specific requirements and guidelines associated with each standard to ensure full compliance within the applicable jurisdiction.
What Kinds of Medical Data Security Software Should You Use?
To ensure robust security for medical data, healthcare organizations should consider implementing the following software solutions to secure healthcare data:
Data encryption solutions
Encryption helps protect sensitive medical data by converting it into a secure format that can only be accessed with the appropriate decryption key. Such solutions ensure that even if the data is compromised, it remains unreadable and unusable to unauthorized individuals.
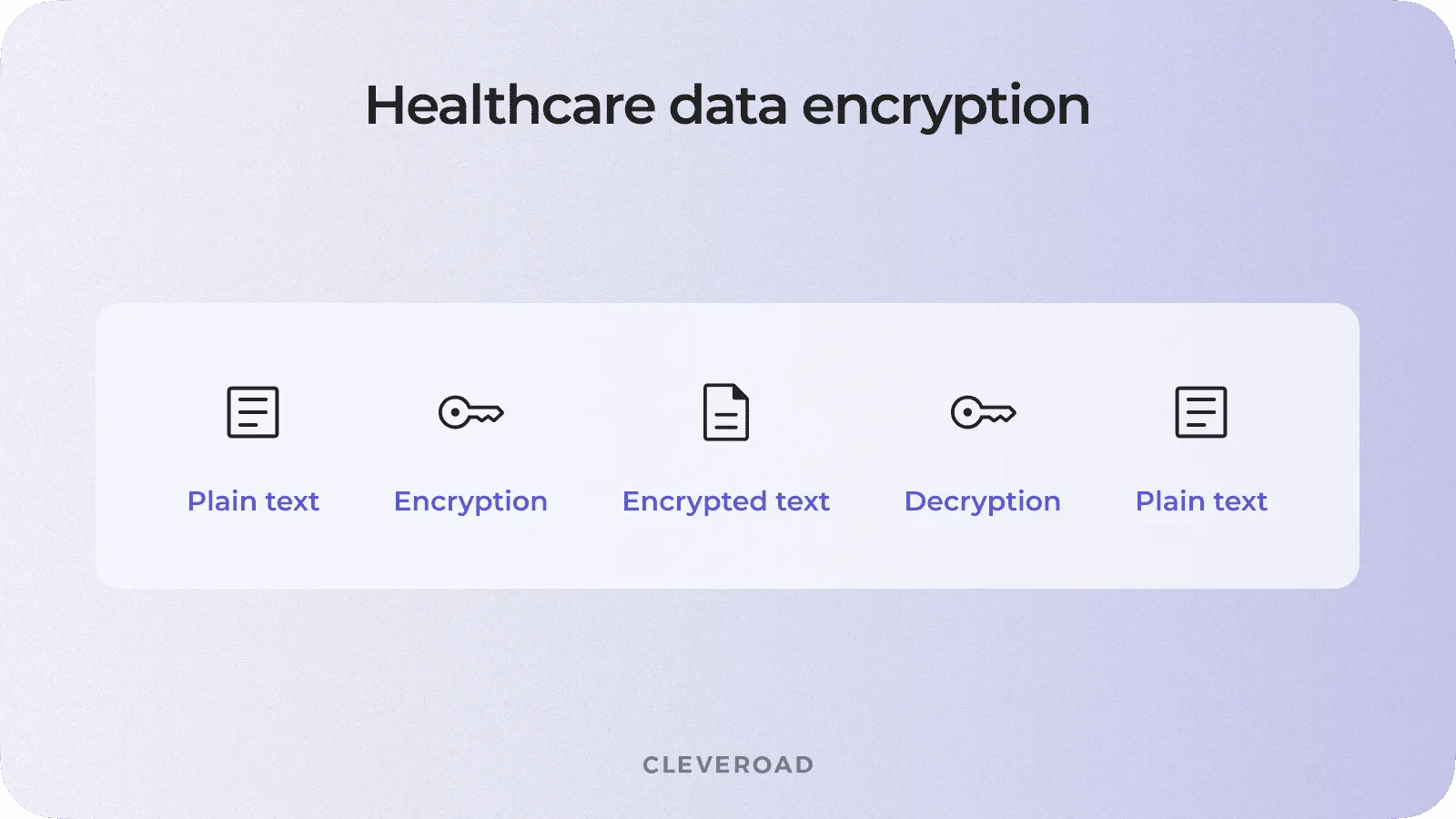
Healthcare data encryption flow
Security Information and Event Management (SIEM) solutions
With such solutions, you can get real-time monitoring and analysis of security events within an organization's network. They help identify potential threats, detect anomalies, and respond promptly to security incidents, enhancing the overall security posture.
Security and compliance management solutions
They may serve as your dedicated assistants in managing data security measures in healthcare and ensuring compliance with relevant regulations such as HIPAA, GDPR, and other industry-specific standards. With these solutions, you get features like policy management, access controls, and audit trail capabilities to support adherence to security and privacy requirements.
System monitoring apps
Businesses can require this type of solution to monitor network activities, log events, and detect any unauthorized access attempts or suspicious behavior. You can also get insights into potential security threats and allow for proactive security measures to be taken.
Data backup and recovery solutions
Robust health information data security backup and recovery solutions help in safeguarding medical data by creating regular backups and providing mechanisms for quick data restoration in case of accidental deletion, hardware failure, or cyber-attacks.
Antivirus/Malware/Spyware apps
Deploying reliable antivirus, malware, and spyware applications helps protect against malicious software and other cyber threats. These applications scan systems, detect and remove malware, and prevent unauthorized access to sensitive medical data.

Best access management practices
Why should you build custom healthcare data security solutions?
Building custom data protection and security in healthcare solutions offers several advantages over off-the-shelf software, such as:
- Better control. Custom solutions allow healthcare organizations to have greater control over the security measures implemented. They can tailor the solution to their specific needs, ensuring that all critical aspects of data security are addressed effectively.
- Tailored protection. With bespoke software, it is possible to implement security measures that are specifically designed to address the unique risks and requirements of the medical industry. This tailored approach enhances the overall protection of sensitive medical data.
- Improved compliance. Software engineers design healthcare solutions with a deep understanding of regulatory requirements, such as HIPAA or GDPR, ensuring compliance from the ground up. By integrating regulatory measures into the custom solution, organizations can minimize the risk of secure healthcare data breaches and associated penalties.
- Seamless integration. From-scratch software can be seamlessly integrated with existing systems and infrastructure within the healthcare organization. This integration simplifies workflows, reduces data security vulnerabilities, and enhances operational efficiency.
Thus, it is wiser to implement a custom medical solution that fully reflects your business requirements.
Discover custom telemedicine app development cost in our utter guide
Cleveroad Experience in Data Security in Healthcare Software Systems
At Cleveroad, a healthcare software development company with over 11 years of experience in IT, we put the critical importance of data security in healthcare and telemedicine systems first. Our team of certified Solution Architects and experienced software engineers has proficiency in creating secure and compliant medical solutions, such as Telemedicine software, EHR, EMR/EPR & Patient Portals, electronic prescribing systems, QMS for medical device manufacturers, hospital management software, etc.
To ensure the security of healthcare software systems, we follow our own strategies and best security practices to guarantee data protection in healthcare and telemedicine systems.
Here are some key strategies and data security measures the Cleveroad team employs:
- Adherence to industry-specific regulations and standards, such as HIPAA, GDPR, and PIPEDA, to ensure that our healthcare solutions comply with the necessary privacy and security requirements.
- Implementing robust authentication mechanisms, including two-factor authentication, to verify user identities and enhance access control, reducing the risk of unauthorized access to sensitive data.
- Applying encryption techniques to protect sensitive data at rest and in transit. By encrypting data, we ensure that even if it is compromised, it remains unreadable and unusable to unauthorized individuals.
- New solutions integrate firewalls, intrusion detection systems, and secure Wi-Fi protocols to safeguard the network infrastructure from external threats and unauthorized access attempts.
- Conducting regular security audits and risk assessments to identify potential vulnerabilities and mitigate any risks proactively. This allows us to maintain a robust security posture for our healthcare software systems.
- Building reliable data backup mechanisms and disaster recovery plans to ensure the availability and integrity of healthcare data. This helps mitigate the impact of data loss or system failures, allowing for quick restoration and continuity of operations.
- Guaranteeing the security and encryption of communication channels within our healthcare solutions. By utilizing secure protocols like Transport Layer Security (TLS), we protect sensitive data during transmission, including video conferencing, messaging, and file transfers.
At Cleveroad, we prioritize healthcare data security in all stages of our software development process. By implementing industry best practices and leveraging our experience, you’ll receive robust and secure healthcare solutions that meet the unique requirements of your medical business and ensure the confidentiality and integrity of patient data.
Let us introduce our practical case studies in ensuring data security by Cleveroad:
IoT-based System for Monitoring EKG and Blood Oxygen Level
Our client, a US-based manufacturer of IoT devices for ECG heart monitoring and pulse oximeters, sought to develop a mobile application integrated with these devices. The goal was to enable users to monitor EKG and check blood oxygen levels directly on their phones. Additionally, they needed a solution to sell the devices online. Cleveroad was chosen as an experienced technology partner to develop the software and fulfill these requirements. What goals we’ve accomplished:
- Secure and smooth integration of EKG devices and pulse oximeters with mobile apps.
- Positive feedback from doctors and patients for the reliable and portable solution
- Expansion of business opportunities through the ability to offer the software to end users and healthcare providers, supported by an e-commerce platform and a forum for medical professionals.
Explore IoT-based System for Monitoring EKG and Blood Oxygen Level case in more detail
Clinic Management System for Rehab Services Provider
A US-based rehab clinic that provides remote care and online consultation. They were using a third-party Electronic Medical Record (EMR) system distributed as a Software-as-a-Service (SaaS) solution. However, they found that approximately 40% of the included features were unnecessary, leading to excessive bills. To address this, they sought a technical partner to develop a custom platform that would offer flexibility and better meet their specific needs. We’ve provided the client with the following outcomes:
- Data migration and solution deployment on HIPAA-compliant AWS cloud hosting to ensure the security and confidentiality of patient information.
- A robust and fault-tolerant platform that optimizes schedule management prevents schedule conflicts, and aligns with the best healthcare practices, enhancing overall workflow efficiency.
- Safe and successful health data migration, ensuring compliance with HIPAA and other data security requirements for US-based clinics. This provides the customer with a secure solution and mitigates legal risks.
Explore Clinic Management System case in more detail
Why is Cleveroad your reliable business partner in healthcare software development?
- Solid expertise in healthcare software development. We understand the industry-specific challenges and requirements of the healthcare business.
- Data security focus. Our team prioritizes data security in all our solutions, ensuring compliance with industry standards and regulations, such as HIPAA, HITECH, TX-HB300, CCHIT, HL7, CDA, and CCD.
- Tailored solutions. We offer custom telemedicine software development services to meet workflows specific to our healthcare clients' needs, providing enhanced data security, high scalability, and flexibility.
- Cost and time efficiency. We guarantee to deliver medical solutions within agreed-upon timelines, helping our customers optimize their resources.
- Dedicated support. Cleveroad experts provide ongoing support and maintenance to ensure smooth operation and data security of the implemented solutions.
Secure your healthcare data
Book a call with our domain expert to ensure robust data protection of your healthcare system
Data security in healthcare refers to the measures and practices implemented to protect sensitive patient information and healthcare data from unauthorized access, breaches, and cyberattacks. It involves safeguarding electronic health records, financial data, and personal information and ensuring compliance with regulatory requirements.
To secure healthcare data, several key approaches can be implemented. These include conducting risk assessments and threat identification, implementing data encryption and access control measures, complying with regulatory requirements such as HIPAA, providing personnel education and awareness, securing network architecture, implementing backup and disaster recovery planning, securing mobile devices, and collaborating with experienced technical providers.
Data security is crucial in healthcare due to the sensitive nature of patient information. Breaches and unauthorized access to healthcare data can have severe consequences, including potential harm to patients, loss of trust, legal and financial implications, and damage to the reputation of healthcare establishments. Prioritizing data security helps protect patient privacy, ensure compliance with regulations, maintain the integrity of healthcare systems, and safeguard the overall well-being of individuals.
To secure data in healthcare, various measures can be implemented. These include implementing robust access controls, strong authentication protocols, data encryption techniques, utilizing security information and event management (SIEM) solutions, conducting regular security audits and risk assessments, ensuring data backups and disaster recovery plans are in place, and employing antivirus, malware, and spyware applications.
Data security in health centers is achieved through a combination of technical measures, policies, and procedures. This includes implementing secure network architectures, utilizing encryption technologies, implementing access controls and authentication mechanisms, conducting regular security assessments, ensuring compliance with regulatory standards like HIPAA, training personnel on data security best practices, and collaborating with experienced technical providers for expertise and support.
One of the biggest threats to the security of healthcare data is the risk of cyberattacks, including ransomware attacks, data breaches, and unauthorized access. Cybercriminals often target healthcare establishments due to the value of sensitive patient information. Insider threats, such as internal employees or contractors mishandling data or engaging in malicious activities, can also pose significant risks to data security in healthcare.

Evgeniy Altynpara is a CTO and member of the Forbes Councils’ community of tech professionals. He is an expert in software development and technological entrepreneurship and has 10+years of experience in digital transformation consulting in Healthcare, FinTech, Supply Chain and Logistics
Give us your impressions about this article
Give us your impressions about this article
