Healthcare Cybersecurity Frameworks: The Definition, Examples and Implementation
Updated 27 Jun 2023
16 Min
3116 Views
Just like in any other industry, cyber attacks in healthcare are quite common. Healthcare's vulnerable to security threats. And there are lots of specific risks, as well as security risks, for health organizations to address.
The healthcare industry involves a lot of sensitive user data, and it often becomes a target for cyberattacks. And it’s a business’ responsibility to keep it safe if they don’t want to suffer both monetary and reputational losses. Nevertheless, security breaches cost $6 trillion for healthcare companies due to a lack of healthcare cybersecurity awareness and little attention to data protection frameworks.
In this guide, we're going to find out what exactly are the security healthcare frameworks, and how to apply them in the field. Along with getting acquainted with widely-known cybersecurity frameworks (CSF).
Common Cybersecurity Healthcare Threats
Before covering popular cybersecurity frameworks, you need to know your enemy, namely, be aware of the main threats that can harm your healthcare business.
Malicious Network Traffic. One of the most widespread threats is suspicious links and files received from the network. This threat first gains access to the network from an application to a hostile web page service and then closes the network and performs dangerous operations (for example, downloading malicious software).
Man-In-The-Middle Attack. The main idea is that attackers interrupt an ongoing conversation or data transfer, injecting themselves in and acting like a legitimate part of the conversation, stealing confidential and other important user data.
Address Resolution Protocol Cache Poisoning. ARP is the way to fool your computer since an attacker injects incorrect data into your network that translates into IP. After that, your computer thinks that the attacker’s computer is a legitimate network gateway, and as a result, it has full access to all your information.
HTTPS Spoofing. This attack method includes cloning a real website with HTTPS but changing some details like changing English “e” to Cyrillic “е” in the URL address. As a result, you visit a fake website riddled with fishing software that steals your valuable and confidential data.
Ransomware. Another infamous way of a cyberattack is when the victim's files are encrypted so the attacker can extort money in exchange for valuable data. Besides information encryption, this attack can block access to whole computer systems, paralyzing the work of the business.
Phishing. The last cyberthreat that you can meet every day when entering the web. Attackers produced personalized emails using data they extract from websites, social media, and many other sources. The main purpose of these letters is to raise the recipient’s curiosity, induce stress, or sometimes appeal to the victim’s vanity.
Now, when you know what can harm your business workflow and reputation, it’s time to talk about tools that aimed to protect you from the abovementioned threats.
Delve into more details concerning powerful healthcare data security
What Is Healthcare Cybersecurity Framework?
In general, a cybersecurity framework (CSF) is a guide, based on already existing guidelines and practices. It helps organizations with reducing cybersecurity risks in healthcare and other fields and with maintaining the management process. Besides, an adaptive and effective approach the framework offers helps administrators with managing sensitive data and predicting cybersecurity-related threats.
So, in short, the frameworks are the roadmaps for securing IT systems.
But a framework doesn't equal a prescription. It provides a common language and methods for fighting cyber threats, not claims to be the only way to secure the information.
It’s a living document intended to be updated when the staff learns from its adoption. Same when technologies and risks change. That’s the reason why the CSF focuses on questions organizations need to ask themselves – to manage their risks in the right way. And while technologies, means, and standards may change – the principals remain.
We can define the main goals of healthcare cybersecurity frameworks:
- Describing the current security situation
- Describing target security posture
- Non-stopping improvement
- Assess progress towards target posture
- Communication risk
But what these frameworks consist of? There are three base components that each CSF has and you should be aware about them:
Framework core. It's an arrangement of cybersecurity activities and references, organized to reach a particular outcome. Its function is to enable communication of cybersecurity risks across an organization.
Implementation tiers. They help associations by defining how they see healthcare cybersecurity management. They help to find the right level of thoroughness for a security program and enable communication of cyber risks across an organization.
Profiles. It's arrangements of organizational goals, premises, and assets against the framework core results. They align industry standards and best practices, support prioritization, and measurement according to the business needs.
Cybersecurity in Healthcare: Main Compliance Requirements
All healthcare solutions must comply with the requirements (data protection and others) set by national regulators and ministries. We have compiled a list of the most basic ones so that you understand what your software should correspond to before you enter the market with it in any region.
HIPAA
It’s an organization that sets out requirements for medical applications distributed in the United States (software that processes, records, and stores Protected Healthcare Information) The main requirement is to maintain confidentiality, integrity, and availability of all electronically protected health information.
GDPR
These European personal data protection rules were introduced in 2018, and all healthcare software operating within the borders of the European Union must comply with them. These rules apply to companies that process data (for example, cloud storage) and companies that receive it (e.g social networks).
CCPA
This law is pretty much the same as GDPR but made for the US market. Every company must inform customers about data collecting (and what data is collected), prepare reports on the collected data at the client's request, deleting the collected data at the client's request, and much more.
HiTECH
These regulations were primarily made for various medical EHR systems and valid in The United States of America. In 2013, the clauses of this law were later introduced into the HIPAA Final Omnibus Rule, and now HIPAA compliant apps are equal to HiTECH compliant.
PIPEDA
Applications working in the Canadian market that store and process personal data must comply with PIPEDA. An interesting fact is that if your app is compliant with PIPEDA, it’s most likely compliant with the GDPR since these two laws are quite similar.
Why Use CSF in Healthcare?
Hospitals and other healthcare providers have always been in need for data security and privacy. That's why they apply safeguards to secure sensitive data within an organization and to show compliance according to industry, state, and federal requirements.
Besides, healthcare is the only industry where cybersecurity threats are more dangerous inside healthcare than outside ones. And on top of that, they’re more frequent, according to Verison's report (59% of internal compared to 42% of external incidents).
There are a few reasons for such strangeness, but human error contributes the most. Hospital employees may abuse their access to internal systems and information they store. For instance, it happens when the hospital staff's checking on what procedures celebrities take. No wonder in 6% of breach cases 'just for fun' appears to be the only motivation.
Custom CRM software often comes with different access levels. Check our 'How to Create a Custom CRM Software' article to learn how to develop the best and most secure solution – and breaches will never make it.
So how exactly health information security frameworks help to resolve these matters? CSF helps to identify, detect, respond, protect and recover from the impacts of security threats and their consequences. It's not a set of strict rules for hospitals, but a guideline of best practices of IT security. And healthcare institutions adopt these guidelines to enhance their existing cybersecurity policies.
For example, one of the most popular health cybersecurity framework called NIST. NIST ensures security using its core elements, implementation tiers, and a profile that aligns them by business requirements, financial capabilities, and risk tolerance (you’ll find a more detailed look at common CS frameworks below).
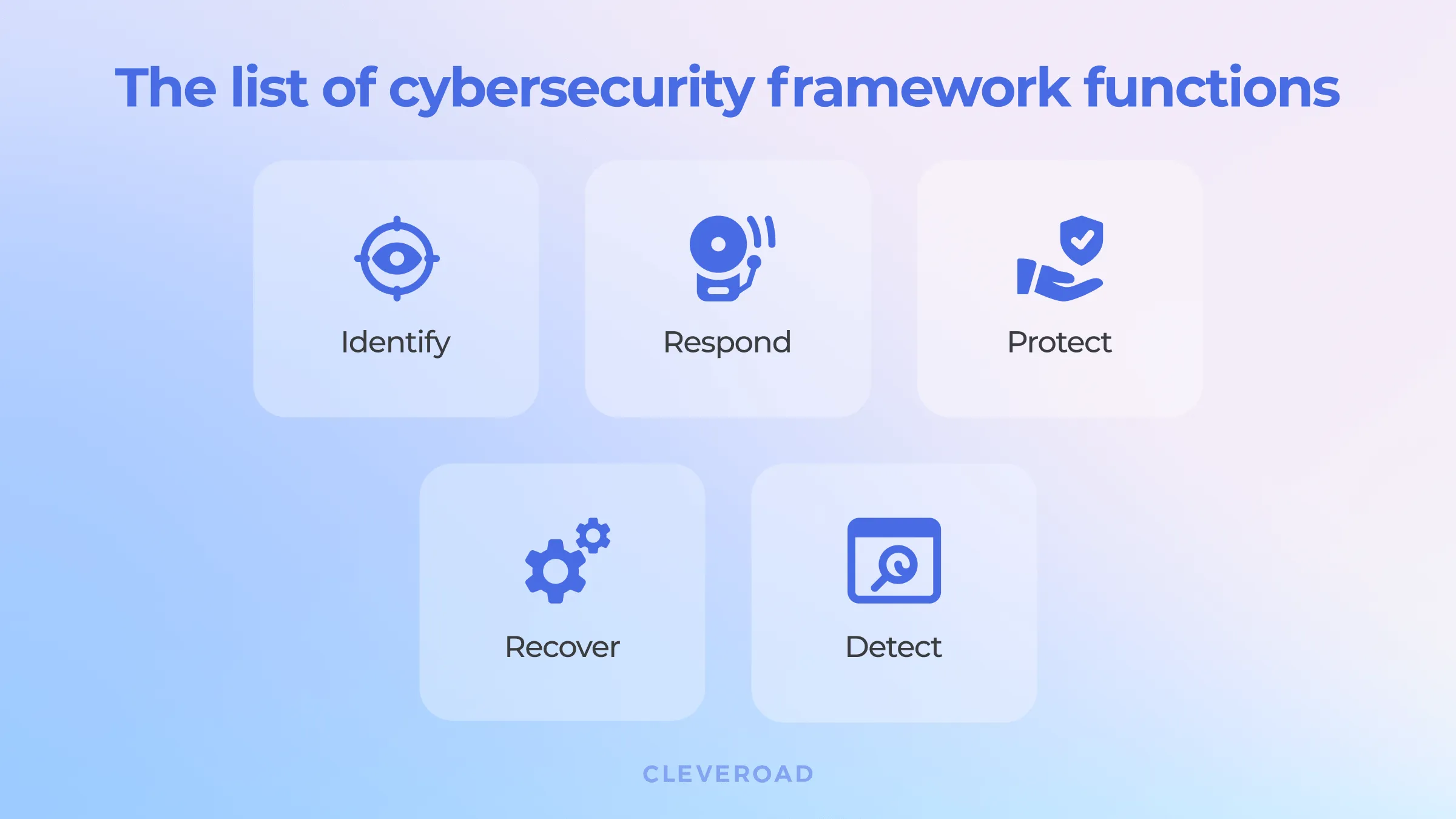
Main functions of cybersecurity frameworks
Cybersecurity frameworks allow external and internal stakeholders to understand and manage healthcare cybersecurity together as a team. It's a tool that helps healthcare entities with aligning business and tech policies. That results in better management of security risks across the whole organization. And, thus, better outcomes are vital when it comes to delivering healthcare services to patients or improved operational efficiency with personnel.
Software testing is a great way to eliminate security breaches. Order QA testing services and make sure the software is well-protected.
Health CSF Implementation
Finally, time to ensure medical cybersecurity and work on CSF adopting. For now, most institutions use a seven-step process when it comes to framework implementation:
- Step 1: Define priorities and organizational components.
- Step 2: Identify current risk management approaches.
- Step 3: Create a risk management profile (Target Profile).
- Step 4: Evaluate the risks.
- Step 5: Make a risk management profile based on the assessment results (Current Profile).
- Step 6: Create an action plan.
- Step 7: Implement the plan.
Now, let’s discuss the steps in more detail.
Prioritize and make the scope
Hospital healthcare cybersecurity begins with defining the main objectives and priorities of the organization. That's required to make strategic decisions regarding the security means and find the systems and tools that support the selected process.
Healthcare providers meet GDPR fist! Find out how to prepare your organization by checking our 'Important EU Directives For Business Owners To Comply With' guide.
And CSF adoption starts with developing a strategy for framing, assessing, monitoring, and responding to risks. This way, a healthcare organization defines how and where to use the framework and analyzes threats and impacts.
Identify Management Approaches
First, the organization figures out what resources they have (tools, technologies, data, personnel). They also identify the appropriate regulatory, looking for authoritative sources like security standards, means, and methods, risk management guidelines, etc.
Second, they calculate the overall risk approach. And define what weak points their means, tools, and systems may have.
Work on a Target Profile
The entity defines its own risk factors and makes an overlay of the healthcare framework. Next, the organization sets the overlay to prevent any unique threats and breaches. Besides, entities may also develop their own Categories and Subcategories to account for unique risks.
They create a Target Profile by pointing out the category and subcategory of the outcomes they are working on from the framework core.
Estimate the risks
The main purpose of this stage is to evaluate the level of risk to the information system. The healthcare organization analyzes the possibility of a security breach and the consequences it may trigger.
It's important to look for incorporate emerging risks as well as for threat and vulnerabilities – to better understand the possible outcome of security events. The estimation can be based on general risk management or previous risk evaluations.
Create a Current Profile
Healthcare entities make a detailed risk assessment and define their current status. This evaluation’s better to be conducted from both the functional area and independently across the organization.
The main goal is to give the organization a clear understanding of current healthcare cybersecurity risks in healthcare – those they may face due to security breaches. So it’s where all the threats and vulnerabilities should be identified and properly documented.
Determine, analyze, and prioritize the gaps
Now, knowing the risks and impacts they bring, healthcare organizations move to a gap analysis. The idea's to compare the actual scores with the target ones. For example, they may create a heat map showing the results in a clear way. And, with this approach, it's easy to highlight the areas to focus on.
Next comes brainstorming – entities find out what to do to fill the gaps between current and target scores.
Make the action plan go live
Finally, having a clear picture of possible cybersecurity issues in healthcare, available defensive means, target goals, a thorough gap analysis plus a list of necessary actions, medical organizations start to implement the framework.
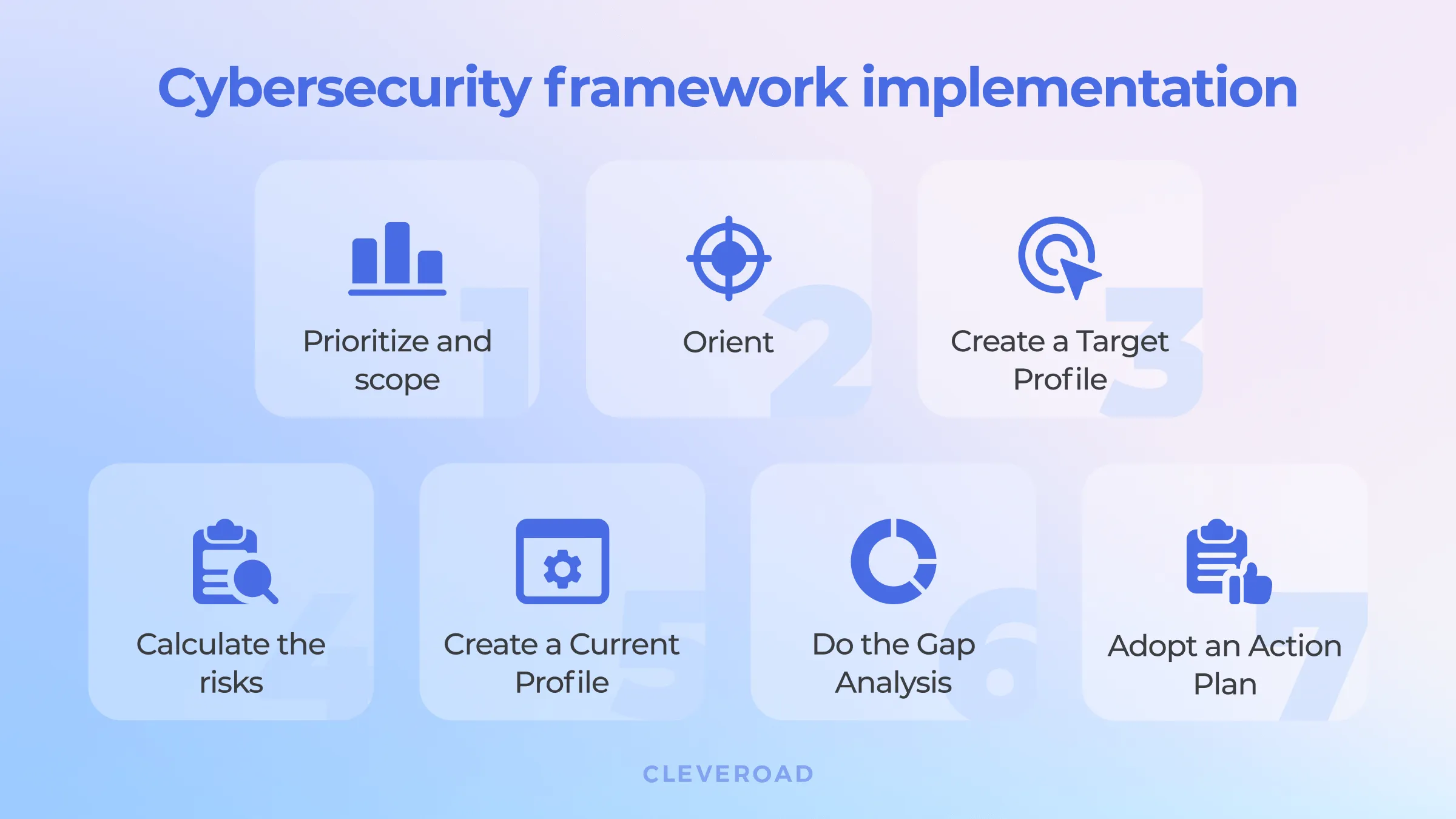
The implementation process, step by step
Still, it doesn’t end just with adopting the action plan. Companies need to organize and check metrics to be aware of their efficiency and make sure that their CSF is fulfilling the company's expectations. It's an ongoing process aimed at getting the maximum benefit and further customizing of the framework to totally meet the business needs.
How to Improve Cybersecurity in Healthcare?
To keep your healthcare business safe from attacks, it’s not enough to use security frameworks only. You need to think several steps forward and implement preventive measures to establish maximum protection against cyberthreats. We’ve gathered several tips to help you out.
Tip #1. Staff Education
One of the main reasons for cyber attacks is human factors, namely the lack of awareness of staff about cyber threats and how they work and can harm a business. Any mistake or negligence in this regard can lead to reputational and financial losses. Health cybersecurity training equips healthcare providers with the knowledge they need to make intelligent decisions and be careful when handling patient data.
Tip #2. Implementing Strict Access Rights
Strict data access controls protect patient data from unauthorized access. Access rights allow only authorized employees of the medical institution to work with data. For maximum security, the following authorization methods should be introduced:
- Password or PIN
- Access via cards or keys
- Access via face, fingerprint, or retina recognition
Tip #3. Data Usage Controls
This tip will help you control and monitor malicious file activity. For example, creating a mental health app, you can implement a system to block unauthorized actions with patient data, such as uploading to the Internet, sending unauthorized e-mail, copying to external drives, or printing.
Tip #4. Log and Monitor Use
Recording all data uses helps to quickly identify unauthorized actions with certain patient data. You will always have a complete summary of information about which users are accessing what information, applications, and other resources, when and from what devices and places. Even if a cyberattack has already happened, the logs will help you quickly establish the breach and take action to eliminate it.
Tip #5. Data Encryption
Encryption is one of the most common ways to improve security posture in enterprises that actively work with confidential data. Encrypting data during transmission and storage allows medical institutions and business partners to make it difficult (and, with a thoughtful approach, make it impossible) for third parties to decrypt data. Although HIPAA gives institutions the choice to encrypt or not, we strongly recommend that you take care of encrypting sensitive data if you value your reputation.
Tip #6. Reducing the Risks of Connected Devices
With the increasing popularity of the Internet of Things, connected devices are no longer limited to mobile phones or tablets. Today they can take any form, from conventional fitness bracelets and blood pressure monitors to cameras used to monitor indoor physical security. For maximum safety:
- Ensure that all connected devices must be on their own separate network
- Ensure that all devices should be monitored continuously for sudden changes in activity levels that could indicate a safety issue.
- Disable and remove nonessential services on devices
- Use multi-factor authentication
- Regularly check and install updates on devices to keep them up to date
Tip #7. Backing Up Data
The consequences of cyber attacks include not only the disclosure of confidential information but also the violation of its integrity or complete removal. Even if your organization is Fort Knox for cyberattacks, the slightest disaster can damage data centers and the precious data in them. This is why you must back up your data on a regular off-site basis with strict controls on data encryption, access, and other best practices to keep your backups safe.
Cybersecurity in Healthcare: Best Framework Examples
HIMSS conducted a Cybersecurity Survey, finding out what medical cybersecurity frameworks are the most popular in the sector. So we’re going to check on five widely used cybersecurity frameworks, and find out why healthcare organizations adopt them.
NIST Healthcare Framework
NIST CFS remains the most popular security framework in many industries, including healthcare. NIST stands for National Institute of Standards and Technology, a USA-based agency that creates lots of tech standards and guidelines, data security included.
NIST maintains quite a few documents, and the best-known are:
- NIST Framework: Improving Critical Infrastructure Cybersecurity
- NIST SP 800-53: Security and Privacy Controls for Federal Information Systems and Organizations
- NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
NIST developed the CSF basing on threat modeling, intelligence, and collaboration. By utilizing it, healthcare institutions not just perform a required analysis of possible risks, but address emerging threats and cooperate with other entities.
HITRUST
HITRUST framework ranks second: 26,4% of healthcare frameworks users claim to follow the guidelines created by the Health Information Trust Alliance.
HITRUST is a private organization led by the best specialists in the healthcare industry. Their main goal is to make data security the basis of information systems. That's why their CSF strives to meet the needs of institutions in providing specific guidance.
Electronic health records system is the best helper to medical entities. Find out more about EHR software development.
The programs include common risk establishment, an assessment and assurance methodology; advocacy and awareness, and so on. Besides, the framework makes use of the ISO/IEC 27001:2005 Information Security Management system, while supporting non-US business associates.
Critical Security Controls
Critical Security Controls, developed by Center for Internet Security, is a list of practices aimed to prevent or stop the most common healthcare cyber attacks. In CSC, all the controls are listed according to their priority – starting with the most important ones like managing vulnerabilities, building an inventory of assets, etc.
Although the CIS Controls play a great role in security insurance, it's not a stand-alone solution. CIS is mostly used with other CFS, for example, NIST.
ISO 27000 Series
ISO stands for International Organization for Standardization which a non-governmental company that develops standards to support world trade. ISO maintains standards aimed at building and maintenance of an information security management system – ISO/IEC 27000.
This framework can be applied in the healthcare sphere to cope with the challenging and constantly evolving requirements of data security.
COBIT CFS
Control Objectives for Information and Related Technologies (COBIT) framework (developed by ISACA) is an IT governance tool. It allows organizations to fill the gap between control requirements and helps with policy development.
It may seem that COBIT focuses on the effectiveness of the IT sphere, rather than on the security of business issues. Still, lots of companies use the CSF to implement practices provided by other security standards, for example, NIST healthcare cybersecurity framework and ISO27001/2.
For now, healthcare providers like hospitals and insurance companies join other entities (financial institutions, private corporations, governments) in adopting COBIT.
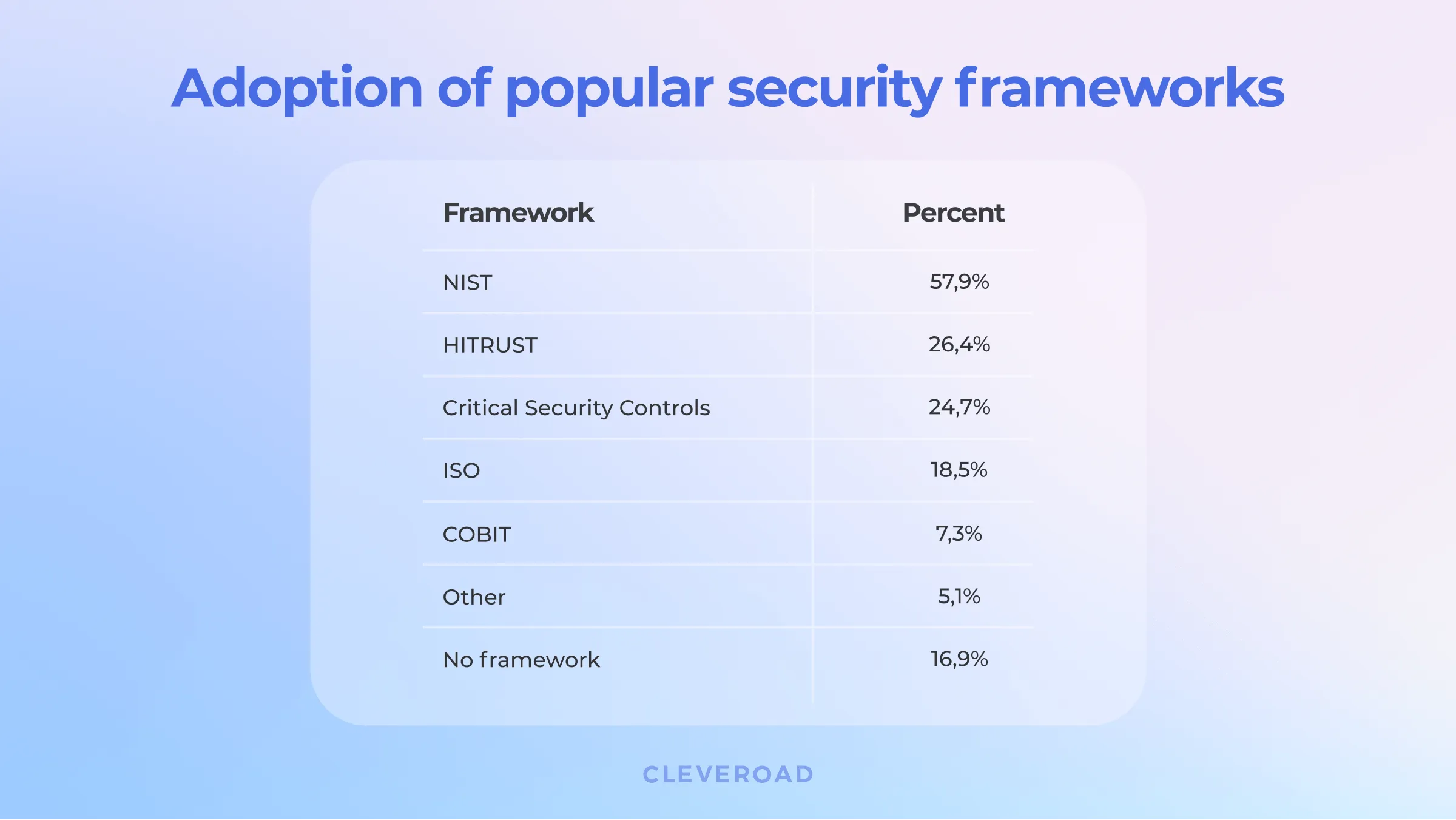
Security frameworks, by usage (Note: Repsonders were able to pick more than one framework)
What Can We Do?
Cleveroad is a healthcare software development company that takes secure matters seriously. So if you need to ensure your website or software security, we’re always here to help.
Our company is the choice of businesses due to the advantages that we provide to them:
- We are fully HIPAA, IEC 62304, ISO 13485/ISO 27001/ISO 27799 compliant
- In our arsenal, there are only modern-day languages and frameworks, secure databases, apply microservices architecture to make apps scalable
- You will be provided with a full development team: mobile and web developers, DevOps, designers, PMs, QA engineers, analysts
- We offer a free initial estimate made by Business Analysts
- We sign a non-disclosure agreement on request
- Every product goes through manual and automated testing to get full test coverage
We are active in healthcare solutions, and we recently added a case to our portfolio in which we talked about the implementation of a mental health app that helps users in the prevention and treatment of various mental disorders and insomnia. The app is called the Nedley Scorecard and is designed with the Nedley Depression and Anxiety Recovery Program in mind.
Our staff is skilled and can help with solving any problem. Contact us and describe your case – and we’ll get back to you in less than 24 hours!
One of the common ways is to adopt a cybersecurity framework.
It helps healthcare organizations reduce cybersecurity risks, internal and external threats. As well as allows administrators to better manage sensitive data and predict cybersecurity-related threats.
Healthcare is the industry where insider threats are more dangerous than outside ones. According to the Verison report (59% of internal compared to 42% of external incidents), they're more frequent, too.
Here are the most common cybersecurity frameworks in healthcare:
- NIST Framework for Improving Critical Infrastructure Cybersecurity
- HITRUST framework
- Critical Security Controls
- ISO 27000 Series
- COBIT CFS
HITRUST framework strives to meet the needs of institutions in providing specific guidance.
The framework includes common risk establishment, an assessment and assurance methodology, advocacy, and awareness.
Each framework has its pros and cons and should be tailored to your business needs. The best approach here is to research each framework's benefits and drawbacks and choose the one that fits your company's needs.
NIST stands for the National Institute of Standards and Technology, a USA-based agency that creates lots of tech standards and guidelines, data security included.
Their framework is called 'NIST Framework for Improving Critical Infrastructure Cybersecurity.'

Evgeniy Altynpara is a CTO and member of the Forbes Councils’ community of tech professionals. He is an expert in software development and technological entrepreneurship and has 10+years of experience in digital transformation consulting in Healthcare, FinTech, Supply Chain and Logistics
Give us your impressions about this article
Give us your impressions about this article